diff --git a/docs/case/case5.md b/docs/case/case5.md
index 8299414d..548b8de6 100644
--- a/docs/case/case5.md
+++ b/docs/case/case5.md
@@ -11,6 +11,7 @@
# 目录
- [项目特点](case5.md#项目特点)
+- [Argo 认证的获取方式: json 或 token](case5.md#argo-认证的获取方式-json-或-token)
- [准备需要用的变量](case5.md#准备需要用的变量)
- [PaaS 部署实例](case5.md#PaaS-部署实例)
- [VPS 部署实例](case5.md#VPS-部署实例)
@@ -32,41 +33,53 @@
* 一条 Argo 隧道分流多个域名和协议 --- 建立一条内网穿透的 Argo 隧道,即可分流三个域名(hostname)和协议(protocal),分别用于面板的访问(http),客户端上报数据(tcp)和 ssh(可选)
* Nginx 反向代理的 gRPC 数据端口 --- 配上证书做 tls 终结,然后 Argo 的隧道配置用 https 服务指向这个反向代理,启用http2回源,grpc(nezha)->h2(nginx)->argo->cf cdn edge->agent
* 每天自动备份 --- 北京时间每天 4 时 0 分自动备份整个哪吒面板文件夹到指定的 github 私库,包括面板主题,面板设置,探针数据和隧道信息,备份保留近 5 天数据;鉴于内容十分重要,必须要放在私库
+* 每天自动更新面板 -- 北京时间每天 4 时 0 分自动检测最新的官方面板版本,有升级时自动更新
* 手/自一体还原备份 --- 每分钟检测一次在线还原文件的内容,遇到有更新立刻还原
* 默认内置本机探针 --- 能很方便的监控自身服务器信息
* 数据更安全 --- Argo 隧道使用TLS加密通信,可以将应用程序流量安全地传输到 Cloudflare 网络,提高了应用程序的安全性和可靠性。此外,Argo Tunnel也可以防止IP泄露和DDoS攻击等网络威胁
 +## Argo 认证的获取方式: json 或 token
+Argo 隧道认证方式有 json 和 token,使用两个方式其中之一
-## 准备需要用的变量
-* 通过 Cloudflare Json 生成网轻松获取 Argo 隧道信息: https://fscarmen.cloudflare.now.cc
+### (方式 1 - Josn):
+#### 通过 Cloudflare Json 生成网轻松获取 Argo 隧道 json 信息: https://fscarmen.cloudflare.now.cc
-
+## Argo 认证的获取方式: json 或 token
+Argo 隧道认证方式有 json 和 token,使用两个方式其中之一
-## 准备需要用的变量
-* 通过 Cloudflare Json 生成网轻松获取 Argo 隧道信息: https://fscarmen.cloudflare.now.cc
+### (方式 1 - Josn):
+#### 通过 Cloudflare Json 生成网轻松获取 Argo 隧道 json 信息: https://fscarmen.cloudflare.now.cc
- +
+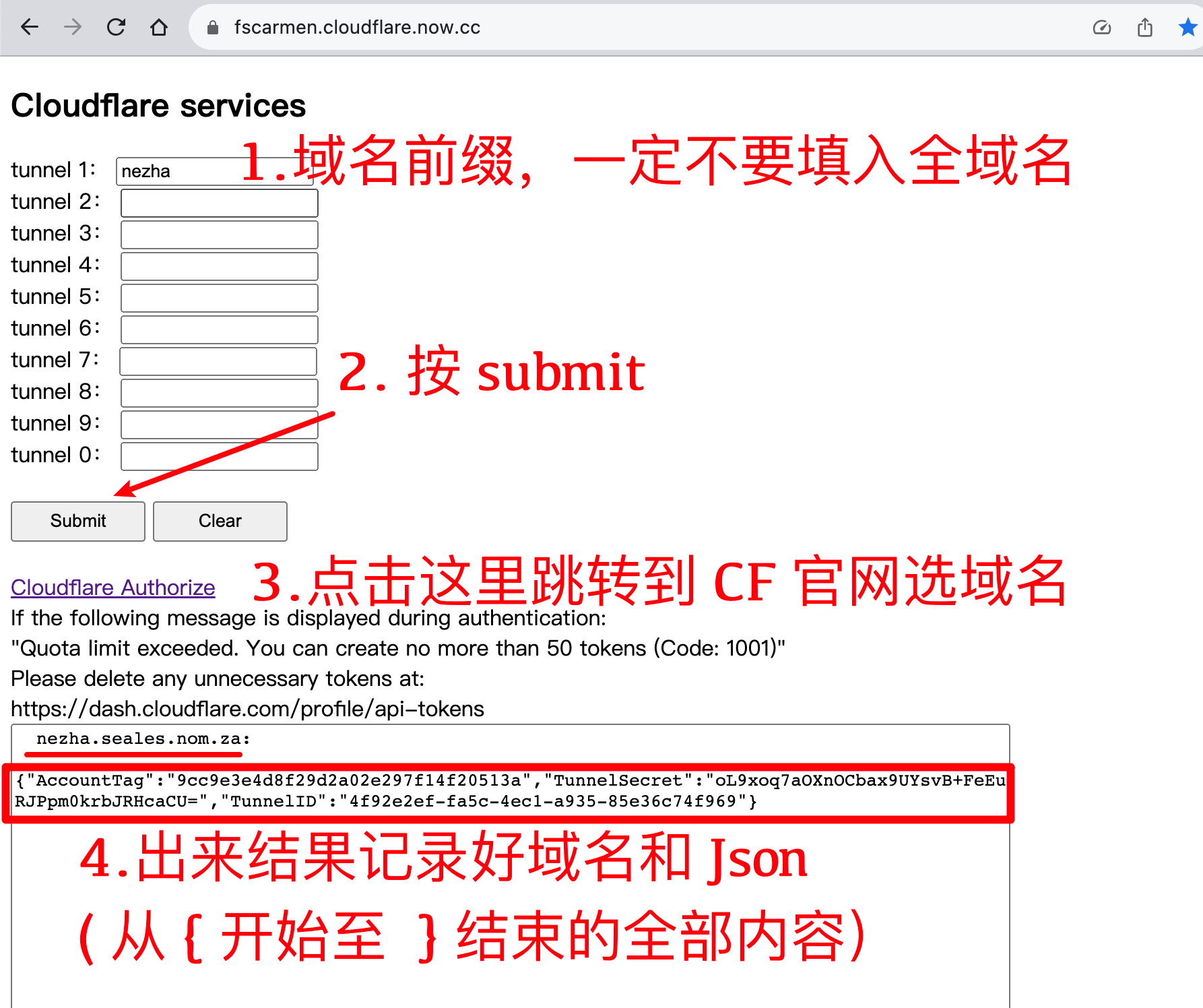 -* 到 Cloudflare 官网,在相应的域名 `DNS` 记录里加上客户端上报数据(tcp)和 ssh(可选)的域名,打开橙色云启用 CDN
+#### 到 Cloudflare 官网,在相应的域名 `DNS` 记录里加上客户端上报数据(tcp)和 ssh(可选)的域名,打开橙色云启用 CDN
-* 到 Cloudflare 官网,在相应的域名 `DNS` 记录里加上客户端上报数据(tcp)和 ssh(可选)的域名,打开橙色云启用 CDN
+#### 到 Cloudflare 官网,在相应的域名 `DNS` 记录里加上客户端上报数据(tcp)和 ssh(可选)的域名,打开橙色云启用 CDN
 -
-
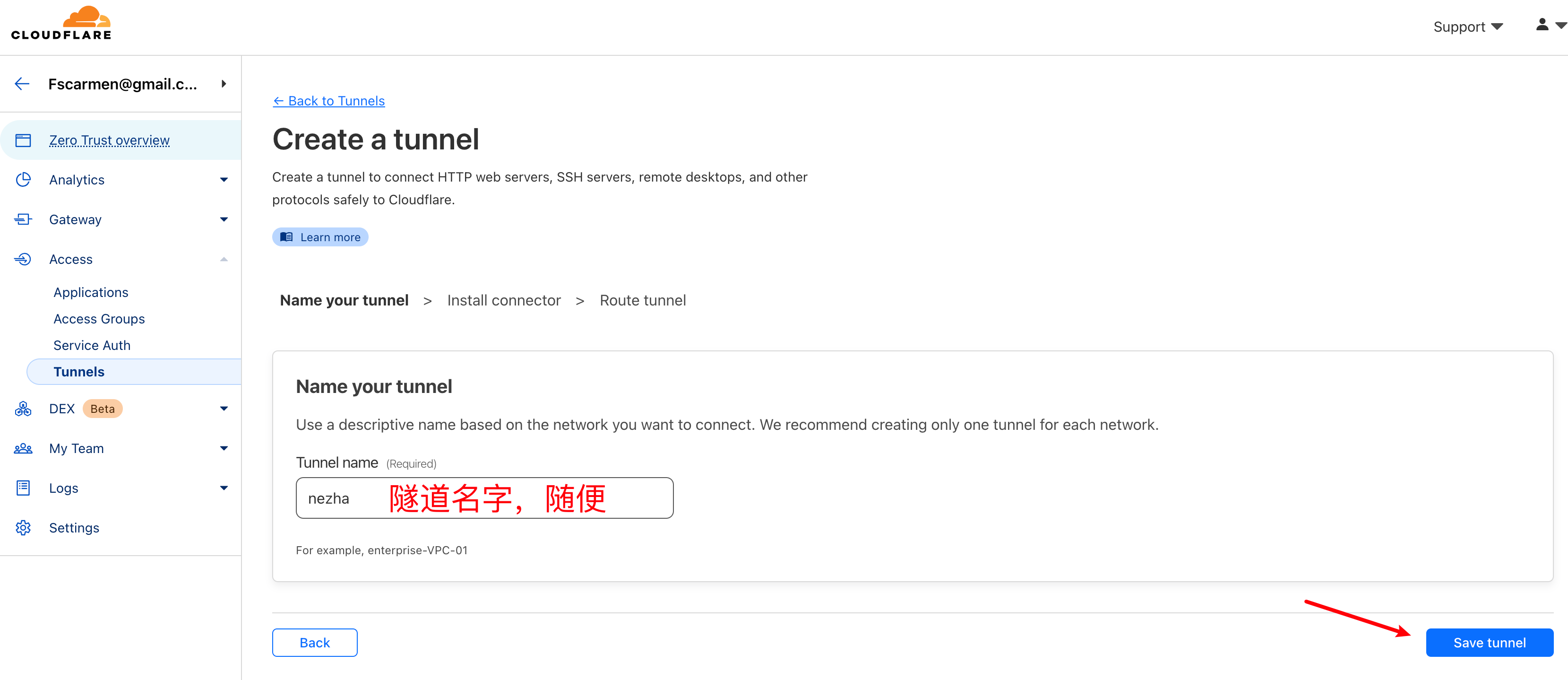
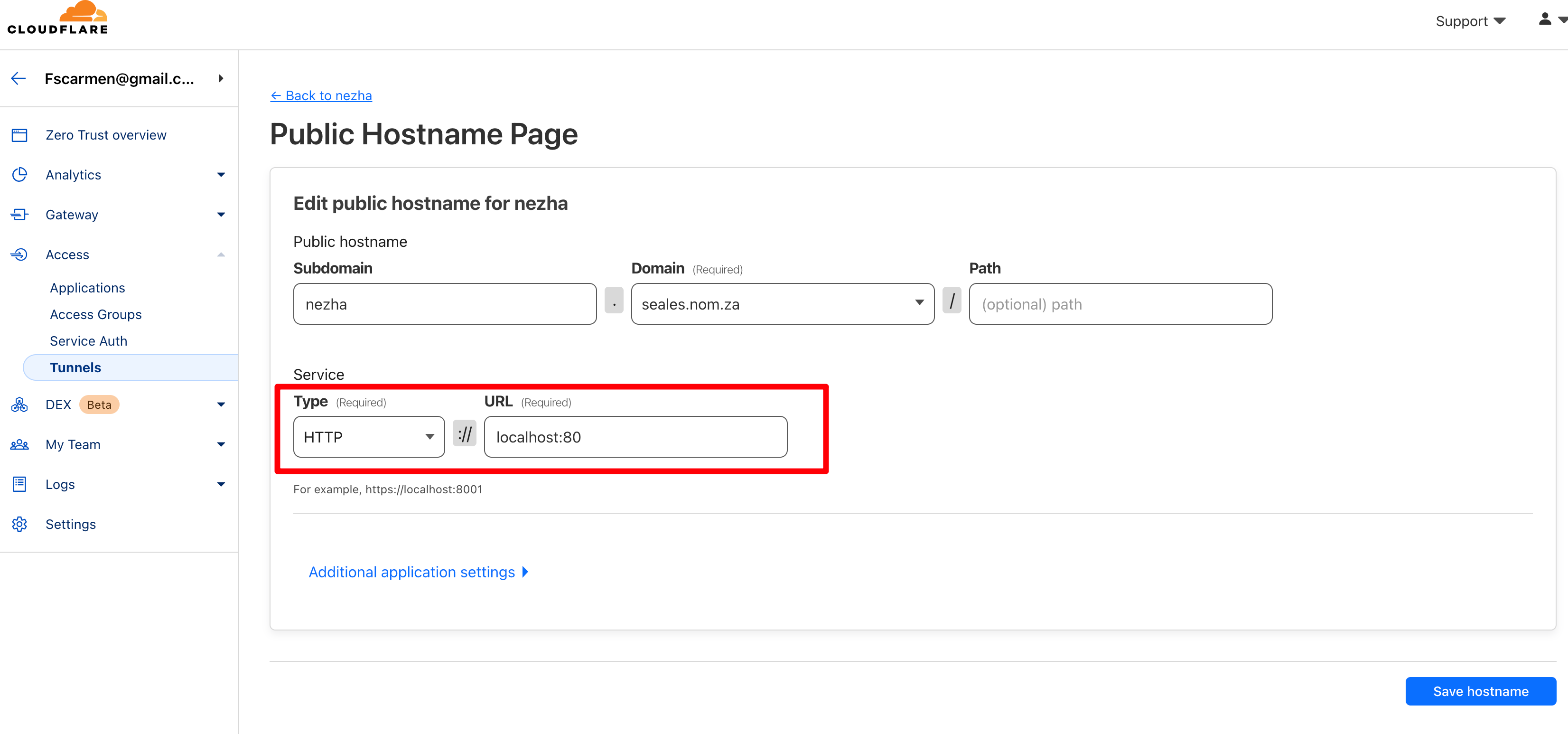
 +### (方式 2 - Token): 通过 Cloudflare 官网,手动生成 Argo 隧道 token 信息
+#### 到 cf 官网:https://dash.cloudflare.com/ ,进入 zero trust 里生成 token 隧道和信息。
+
+
+### (方式 2 - Token): 通过 Cloudflare 官网,手动生成 Argo 隧道 token 信息
+#### 到 cf 官网:https://dash.cloudflare.com/ ,进入 zero trust 里生成 token 隧道和信息。
+
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+
+## 准备需要用的变量
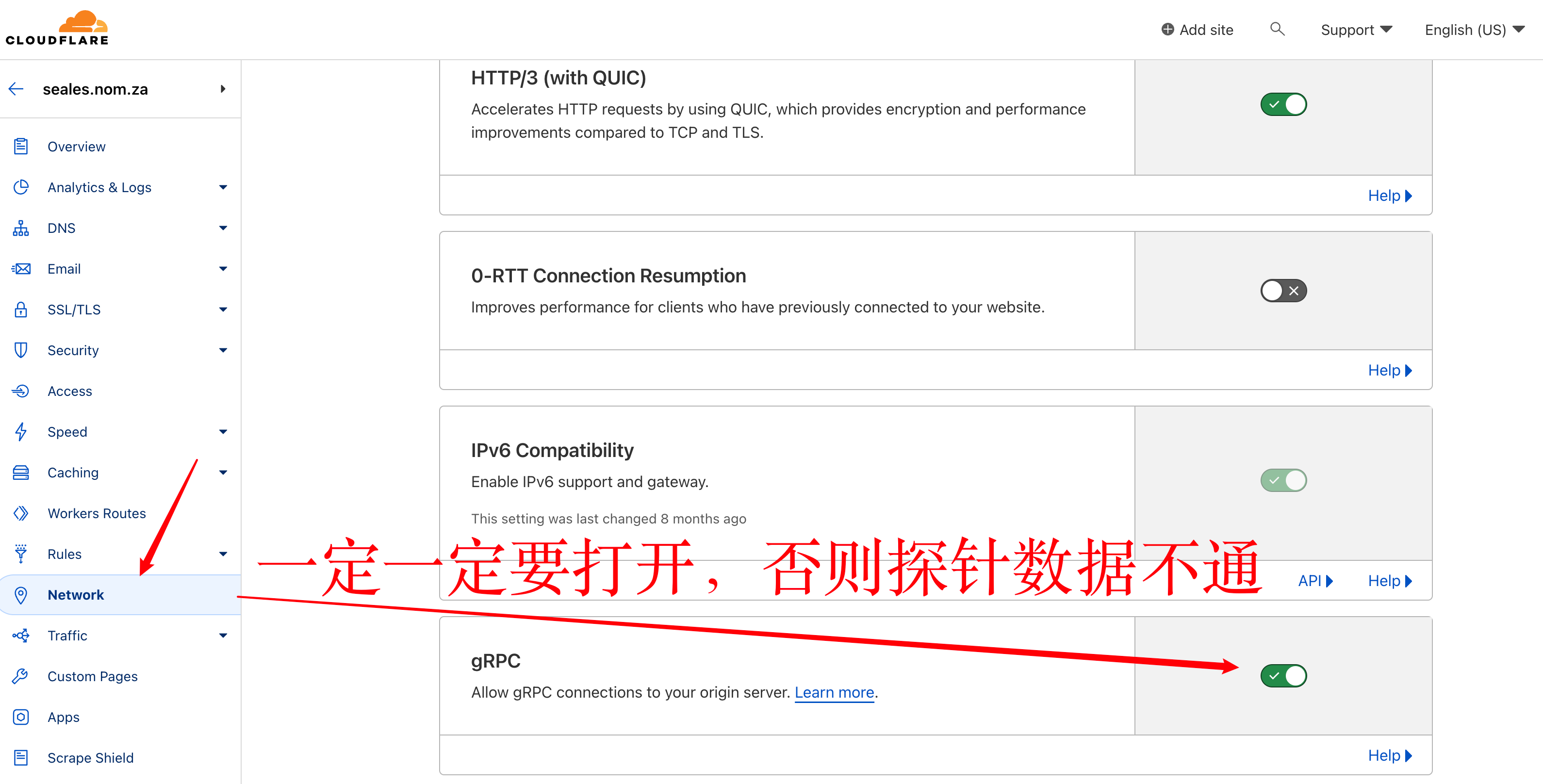
* 到 Cloudflare 官网,选择使用的域名,打开 `网络` 选项将 `gRPC` 开关打开
+
+
+## 准备需要用的变量
* 到 Cloudflare 官网,选择使用的域名,打开 `网络` 选项将 `gRPC` 开关打开
 -
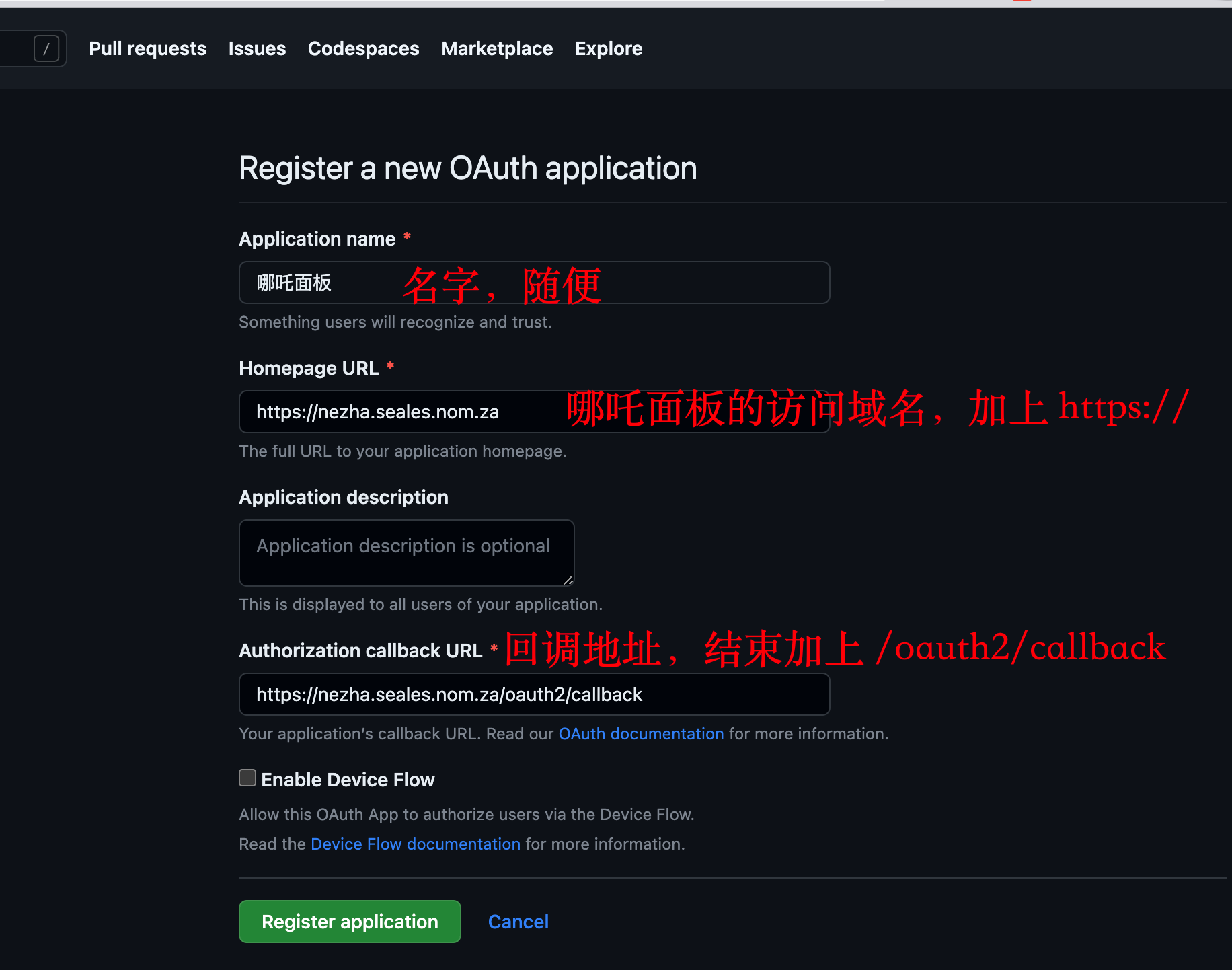
* 获取 github 认证授权: https://github.com/settings/applications/new
面板域名加上 `https://` 开头,回调地址再加上 `/oauth2/callback` 结尾
-
* 获取 github 认证授权: https://github.com/settings/applications/new
面板域名加上 `https://` 开头,回调地址再加上 `/oauth2/callback` 结尾
 -
-
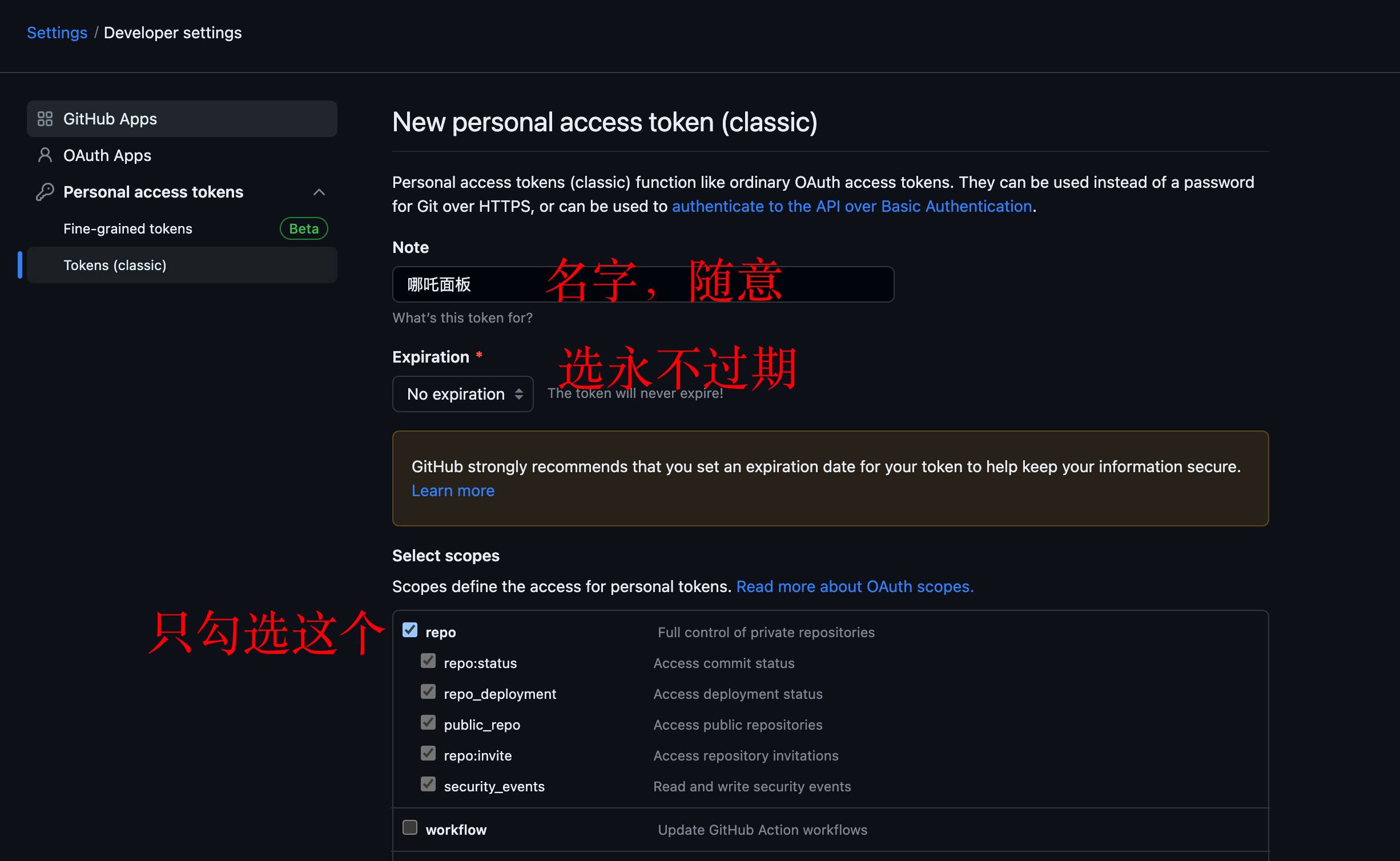
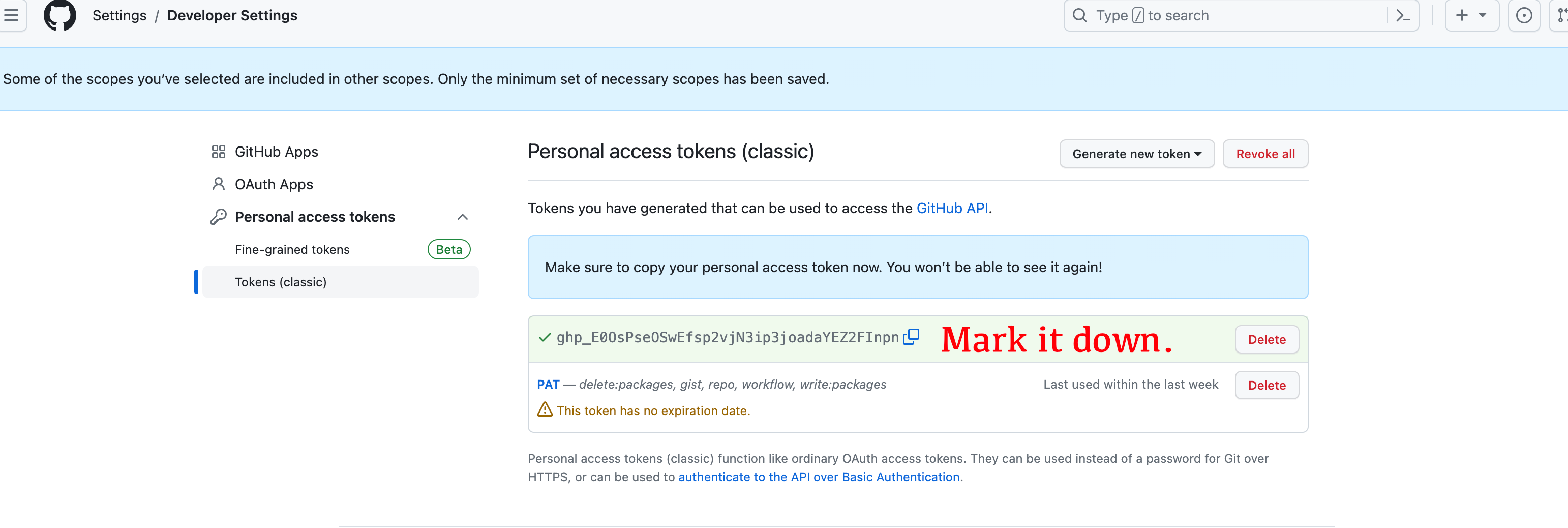
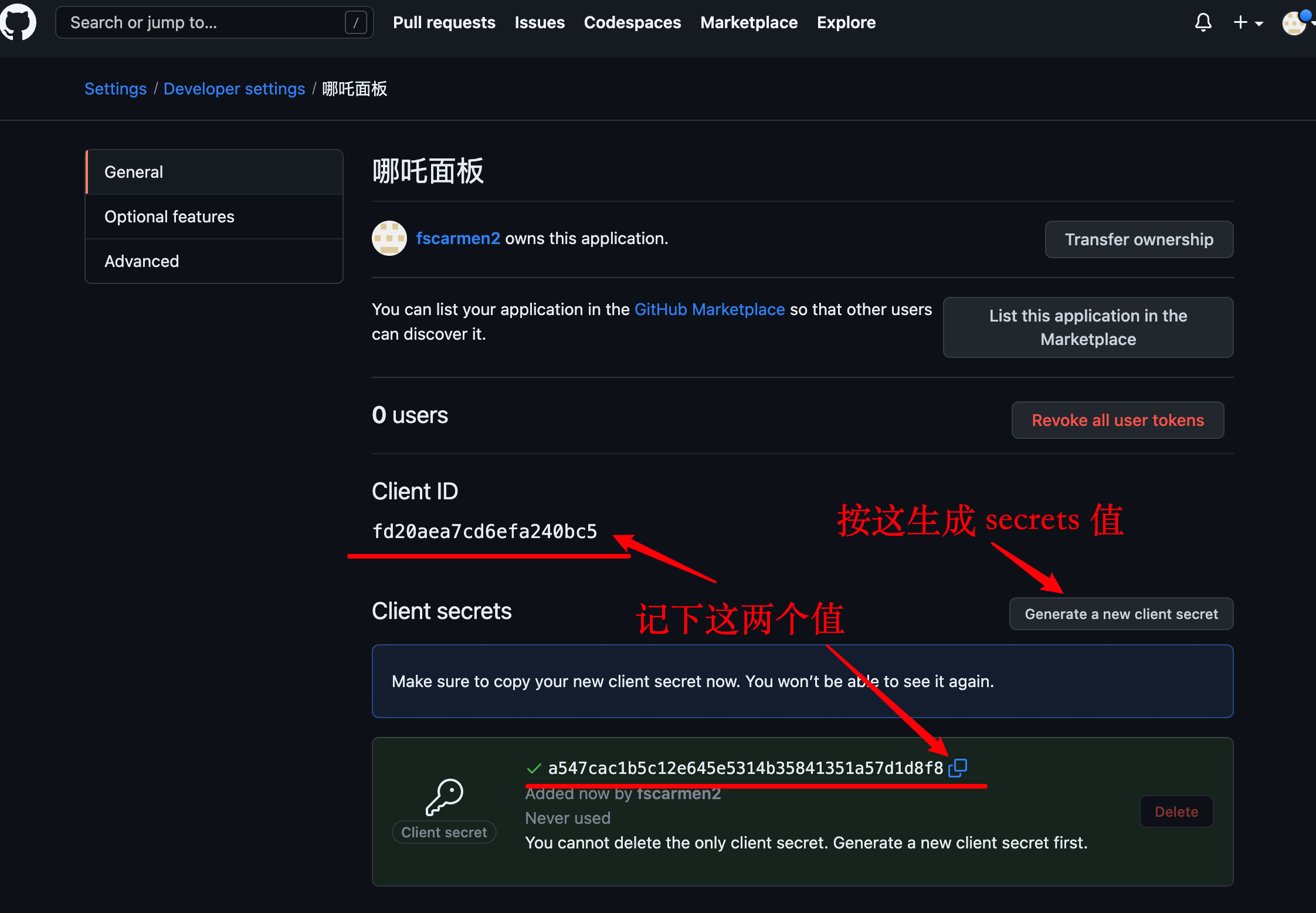 * 获取 github 的 PAT (Personal Access Token): https://github.com/settings/tokens/new
* 获取 github 的 PAT (Personal Access Token): https://github.com/settings/tokens/new
 -
-
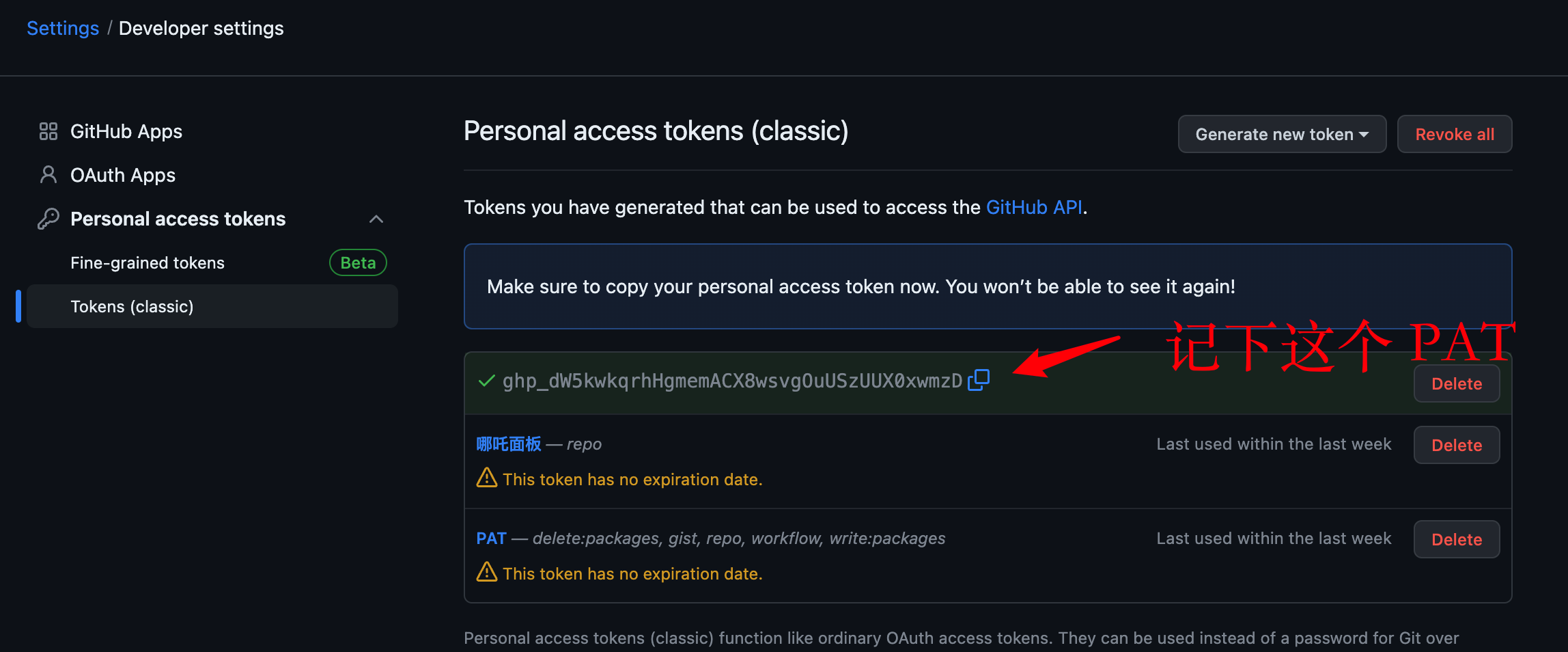 * 创建 github 用于备份的私库: https://github.com/new
@@ -77,7 +90,7 @@
## PaaS 部署实例
镜像 `fscarmen/argo-nezha:latest` , 支持 amd64 和 arm64 架构
-用到的变量
+用到的变量
| 变量名 | 是否必须 | 备注 |
| ------------ | ------ | ---- |
| GH_USER | 是 | github 的用户名,用于面板管理授权 |
@@ -87,7 +100,7 @@
| GH_REPO | 否 | 在 github 上备份哪吒服务端数据库文件的 github 库 |
| GH_EMAIL | 否 | github 的邮箱,用于备份的 git 推送到远程库 |
| GH_PAT | 否 | github 的 PAT |
- | ARGO_JSON | 是 | 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json |
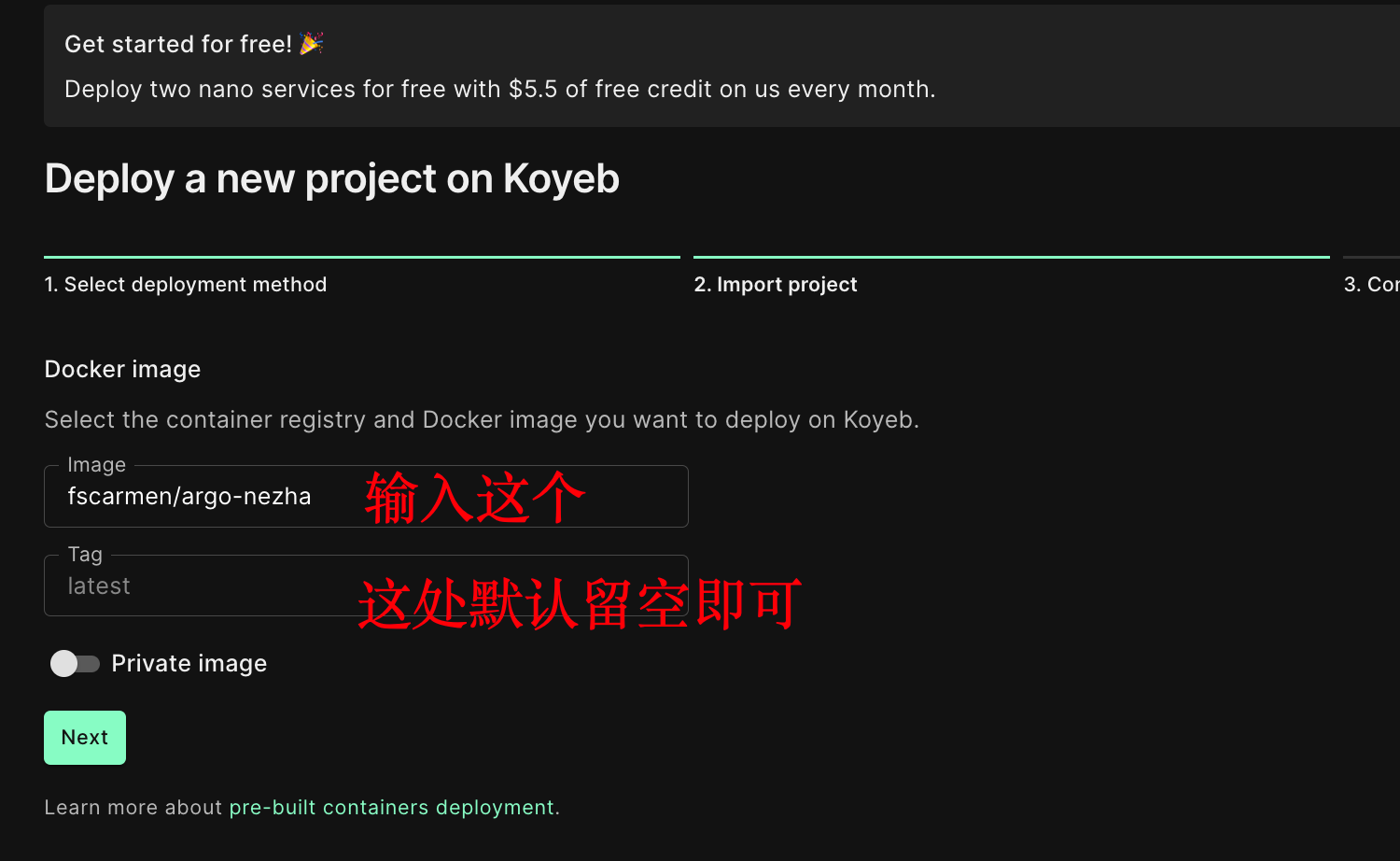
+ | ARGO_AUTH | 是 | Json: 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json
* 创建 github 用于备份的私库: https://github.com/new
@@ -77,7 +90,7 @@
## PaaS 部署实例
镜像 `fscarmen/argo-nezha:latest` , 支持 amd64 和 arm64 架构
-用到的变量
+用到的变量
| 变量名 | 是否必须 | 备注 |
| ------------ | ------ | ---- |
| GH_USER | 是 | github 的用户名,用于面板管理授权 |
@@ -87,7 +100,7 @@
| GH_REPO | 否 | 在 github 上备份哪吒服务端数据库文件的 github 库 |
| GH_EMAIL | 否 | github 的邮箱,用于备份的 git 推送到远程库 |
| GH_PAT | 否 | github 的 PAT |
- | ARGO_JSON | 是 | 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json |
+ | ARGO_AUTH | 是 | Json: 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json
Token: 从 Cloudflare 官网获取 |
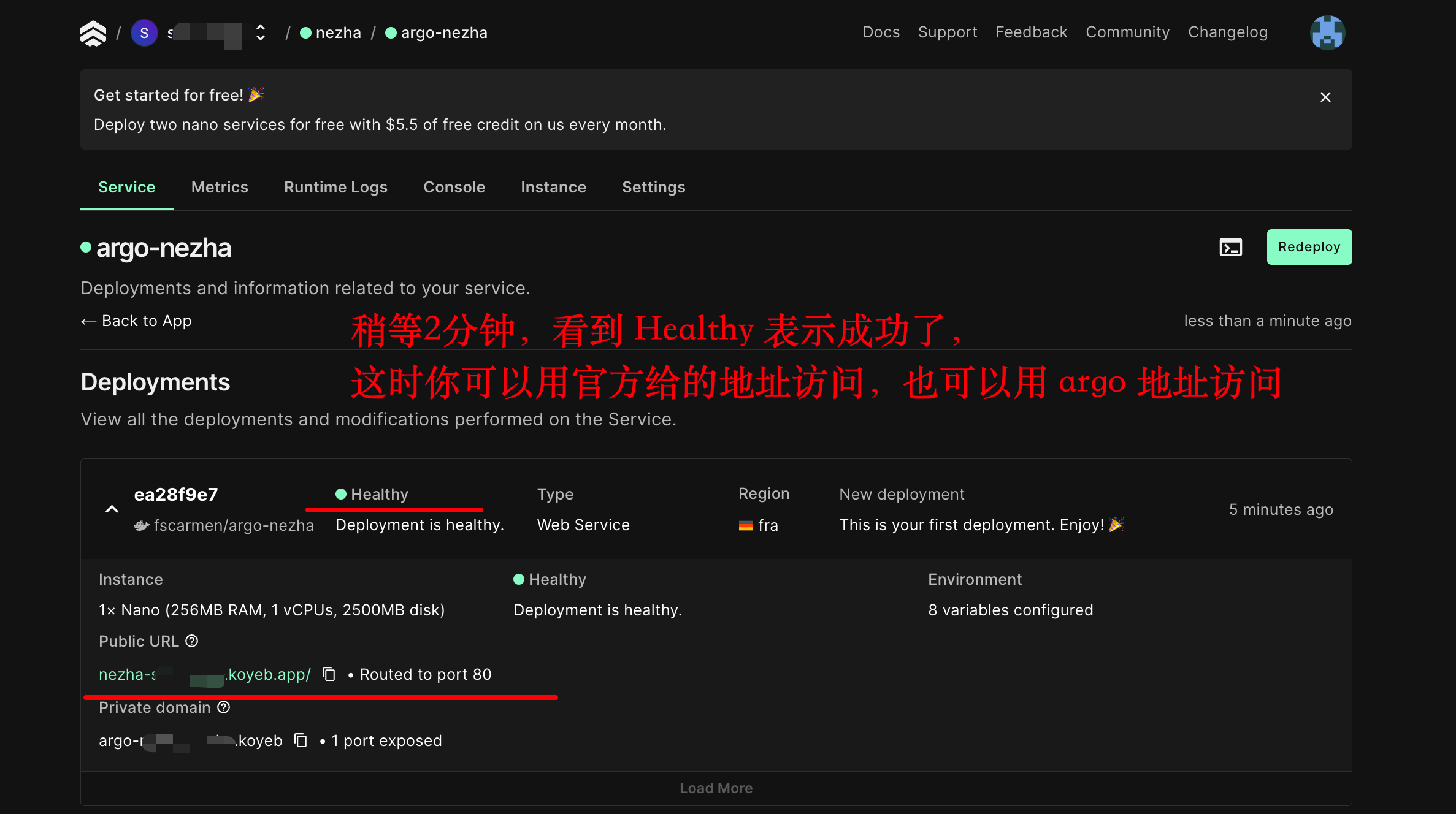
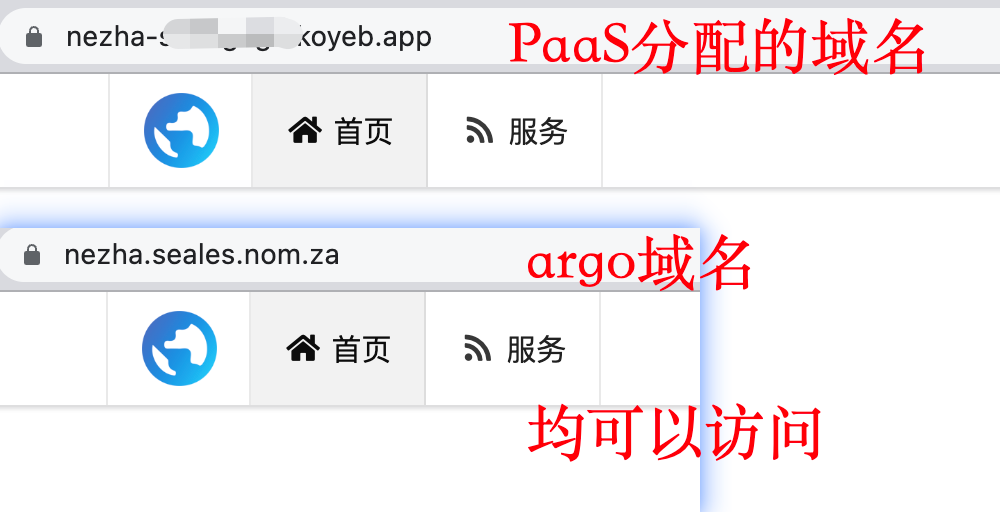
| DATA_DOMAIN | 是 | 客户端与服务端的通信 argo 域名 |
| WEB_DOMAIN | 是 | 面板 argo 域名 |
| SSH_DOMAIN | 否 | ssh 用的 argo 域名 |
@@ -95,10 +108,11 @@
Koyeb
-[](https://app.koyeb.com/deploy?type=docker&name=nezha&ports=80;http;/&env[GH_USER]=&env[GH_CLIENTID]=&env[GH_CLIENTSECRET]=&env[GH_REPO]=&env[GH_EMAIL]=&env[GH_PAT]=&env[ARGO_JSON]=&env[DATA_DOMAIN]=&env[WEB_DOMAIN]=&env[SSH_DOMAIN]=&env[SSH_PASSWORD]=&image=docker.io/fscarmen/argo-nezha)
+[](https://app.koyeb.com/deploy?type=docker&name=nezha&ports=80;http;/&env[GH_USER]=&env[GH_CLIENTID]=&env[GH_CLIENTSECRET]=&env[GH_REPO]=&env[GH_EMAIL]=&env[GH_PAT]=&env[ARGO_AUTH]=&env[DATA_DOMAIN]=&env[WEB_DOMAIN]=&env[SSH_DOMAIN]=&env[SSH_PASSWORD]=&image=docker.io/fscarmen/argo-nezha)
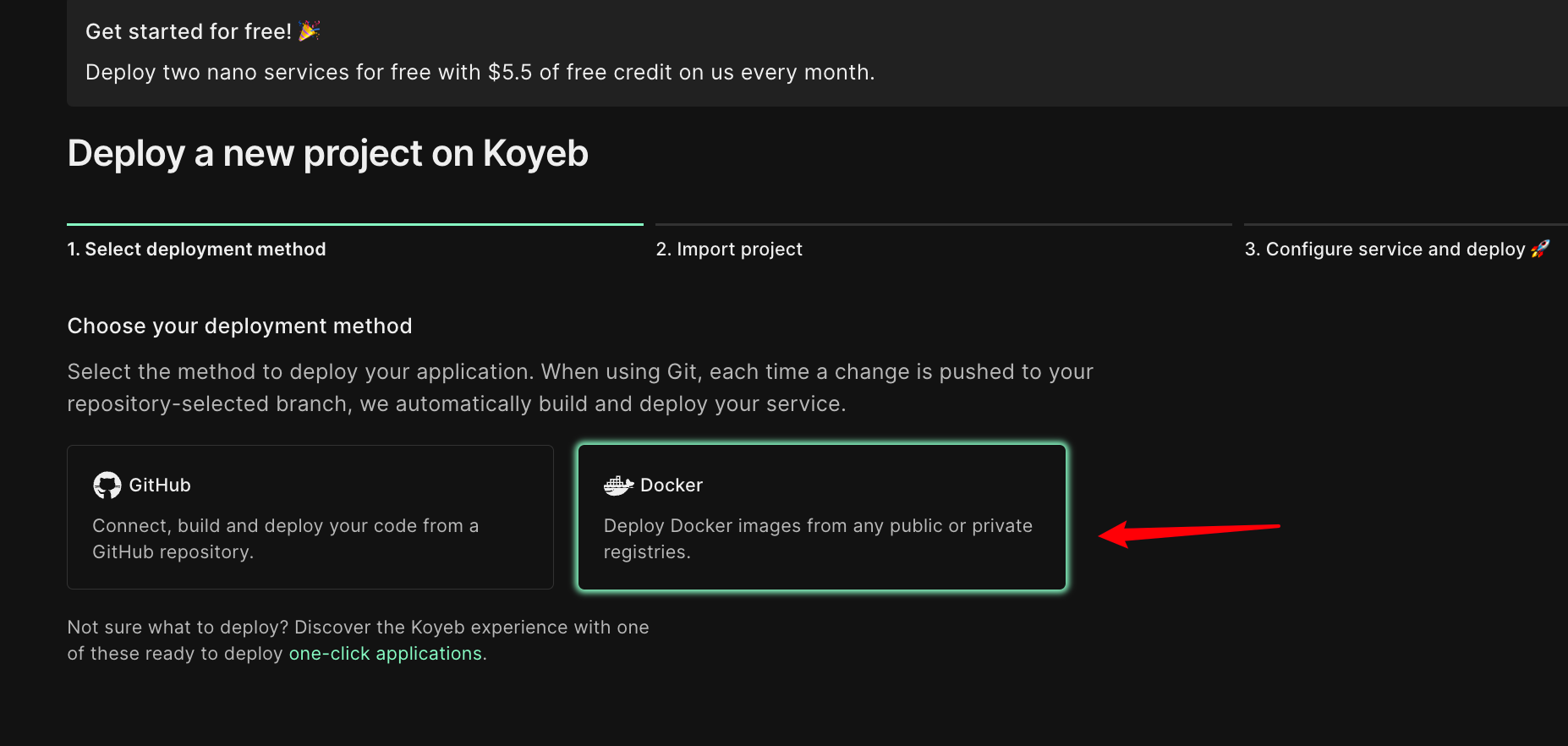
 +
+

 @@ -121,7 +135,7 @@ docker run -dit \
-e GH_REPO=<填自定义的> \
-e GH_CLIENTID=<填获取的> \
-e GH_CLIENTSECRET=<填获取的> \
- -e ARGO_JSON='<填获取的>' \
+ -e ARGO_AUTH='<填获取的 Argo json 或者 token>' \
-e WEB_DOMAIN=<填自定义的> \
-e DATA_DOMAIN=<填自定义的> \
-e SSH_DOMAIN=<填自定义的> \
@@ -144,7 +158,7 @@ services:
- GH_REPO=<填自定义的>
- GH_CLIENTID=<填获取的>
- GH_CLIENTSECRET=<填获取的>
- - ARGO_JSON='<填获取的>'
+ - ARGO_AUTH='<填获取的 Argo json 或者 token>'
- WEB_DOMAIN=<填自定义的>
- DATA_DOMAIN=<填自定义的>
- SSH_DOMAIN=<填自定义的>
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # SSL/TLS 证书的私钥信息
| |-- nezha.pem # SSL/TLS 隐私增强邮件
| `-- restore.sh # 还原备份脚本
-`-- dbfile # 记录最新的还原或备份文件名
+|-- dbfile # 记录最新的还原或备份文件名
+`-- version # 记录当前的面板 app 版本
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* 用 Cloudflare Tunnel 进行内网穿透: https://blog.outv.im/2021/cloudflared-tunnel/
+* 如何给 GitHub Actions 添加自己的 Runner 主机: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner 添加与启动: https://blog.csdn.net/sinat_32188225/article/details/125978331
## 免责声明:
diff --git a/docs/en_US/case/case5.md b/docs/en_US/case/case5.md
index 4ef74355..729b4f04 100644
--- a/docs/en_US/case/case5.md
+++ b/docs/en_US/case/case5.md
@@ -11,6 +11,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
# Catalog
- [Project Features](case5.md#project-features)
+- [How to get Argo authentication: json or token](case5.md#How-to-get-Argo-authentication-json-or-token)
- [Variables to be used](case5.md#prepare-variables-to-be-used)
- [PaaS Deployment Example](case5.md#paas-deployment-example)
- [VPS Deployment Example](case5.md#vps-deployment-example)
@@ -32,6 +33,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
* One Argo tunnel for multiple domains and protocols --- Create an intranet-penetrating Argo tunnel for three domains (hostname) and protocols, which can be used for panel access (http), client reporting (tcp) and ssh (optional).
* Nginx reverse proxy gRPC data port --- with a certificate for tls termination, then Argo's tunnel configuration with https service pointing to this reverse proxy, enable http2 back to the source, grpc(nezha)->h2(nginx)->argo->cf cdn edge->agent
* Daily automatic backup --- every day at 04:00 BST, the entire Nezha panel folder is automatically backed up to a designated private github repository, including panel themes, panel settings, probe data and tunnel information, the backup retains nearly 5 days of data; the content is so important that it must be placed in the private repository.
+* Automatic daily panel update -- the latest official panel version is automatically detected every day at 4:00 BST, and updated when there is an upgrade.
* Manual/automatic restore backup --- check the content of online restore file once a minute, and restore immediately when there is any update.
* Default built-in local probes --- can easily monitor their own server information
* More secure data --- Argo Tunnel uses TLS encrypted communication to securely transmit application traffic to the Cloudflare network, improving application security and reliability. In addition, Argo Tunnel protects against network threats such as IP leaks and DDoS attacks.
@@ -39,17 +41,31 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
@@ -121,7 +135,7 @@ docker run -dit \
-e GH_REPO=<填自定义的> \
-e GH_CLIENTID=<填获取的> \
-e GH_CLIENTSECRET=<填获取的> \
- -e ARGO_JSON='<填获取的>' \
+ -e ARGO_AUTH='<填获取的 Argo json 或者 token>' \
-e WEB_DOMAIN=<填自定义的> \
-e DATA_DOMAIN=<填自定义的> \
-e SSH_DOMAIN=<填自定义的> \
@@ -144,7 +158,7 @@ services:
- GH_REPO=<填自定义的>
- GH_CLIENTID=<填获取的>
- GH_CLIENTSECRET=<填获取的>
- - ARGO_JSON='<填获取的>'
+ - ARGO_AUTH='<填获取的 Argo json 或者 token>'
- WEB_DOMAIN=<填自定义的>
- DATA_DOMAIN=<填自定义的>
- SSH_DOMAIN=<填自定义的>
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # SSL/TLS 证书的私钥信息
| |-- nezha.pem # SSL/TLS 隐私增强邮件
| `-- restore.sh # 还原备份脚本
-`-- dbfile # 记录最新的还原或备份文件名
+|-- dbfile # 记录最新的还原或备份文件名
+`-- version # 记录当前的面板 app 版本
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* 用 Cloudflare Tunnel 进行内网穿透: https://blog.outv.im/2021/cloudflared-tunnel/
+* 如何给 GitHub Actions 添加自己的 Runner 主机: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner 添加与启动: https://blog.csdn.net/sinat_32188225/article/details/125978331
## 免责声明:
diff --git a/docs/en_US/case/case5.md b/docs/en_US/case/case5.md
index 4ef74355..729b4f04 100644
--- a/docs/en_US/case/case5.md
+++ b/docs/en_US/case/case5.md
@@ -11,6 +11,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
# Catalog
- [Project Features](case5.md#project-features)
+- [How to get Argo authentication: json or token](case5.md#How-to-get-Argo-authentication-json-or-token)
- [Variables to be used](case5.md#prepare-variables-to-be-used)
- [PaaS Deployment Example](case5.md#paas-deployment-example)
- [VPS Deployment Example](case5.md#vps-deployment-example)
@@ -32,6 +33,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
* One Argo tunnel for multiple domains and protocols --- Create an intranet-penetrating Argo tunnel for three domains (hostname) and protocols, which can be used for panel access (http), client reporting (tcp) and ssh (optional).
* Nginx reverse proxy gRPC data port --- with a certificate for tls termination, then Argo's tunnel configuration with https service pointing to this reverse proxy, enable http2 back to the source, grpc(nezha)->h2(nginx)->argo->cf cdn edge->agent
* Daily automatic backup --- every day at 04:00 BST, the entire Nezha panel folder is automatically backed up to a designated private github repository, including panel themes, panel settings, probe data and tunnel information, the backup retains nearly 5 days of data; the content is so important that it must be placed in the private repository.
+* Automatic daily panel update -- the latest official panel version is automatically detected every day at 4:00 BST, and updated when there is an upgrade.
* Manual/automatic restore backup --- check the content of online restore file once a minute, and restore immediately when there is any update.
* Default built-in local probes --- can easily monitor their own server information
* More secure data --- Argo Tunnel uses TLS encrypted communication to securely transmit application traffic to the Cloudflare network, improving application security and reliability. In addition, Argo Tunnel protects against network threats such as IP leaks and DDoS attacks.
@@ -39,17 +41,31 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
 -## Prepare variables to be used
-* Easily get Argo tunnel information through Cloudflare Json generation network: https://fscarmen.cloudflare.now.cc
+## How to get Argo authentication: json or token
+The Argo Tunnel authentication methods are json and token, use one of the two methods.
-
-## Prepare variables to be used
-* Easily get Argo tunnel information through Cloudflare Json generation network: https://fscarmen.cloudflare.now.cc
+## How to get Argo authentication: json or token
+The Argo Tunnel authentication methods are json and token, use one of the two methods.
- +### (Methods 1 - Josn):
+#### Easily get Argo tunnel json information through Cloudflare Json Generation Network: https://fscarmen.cloudflare.now.cc
-* Visit Cloudflare website, add the domain name of the client reporting data (tcp) and ssh (optional) in the `DNS` record of the corresponding domain, and turn on Orange Cloud to enable CDN.
+
+### (Methods 1 - Josn):
+#### Easily get Argo tunnel json information through Cloudflare Json Generation Network: https://fscarmen.cloudflare.now.cc
-* Visit Cloudflare website, add the domain name of the client reporting data (tcp) and ssh (optional) in the `DNS` record of the corresponding domain, and turn on Orange Cloud to enable CDN.
+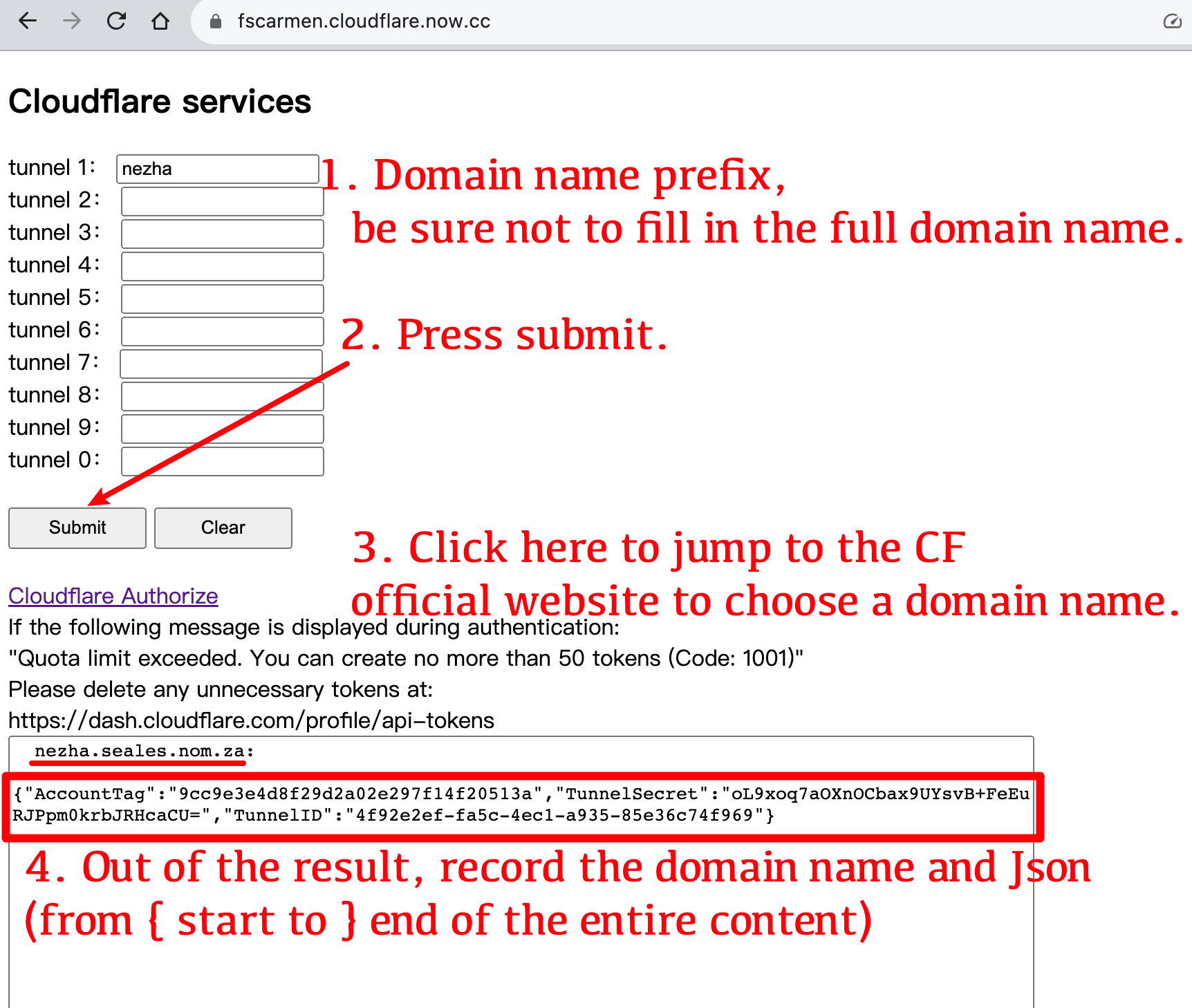 +
+#### Visit Cloudflare website, add the domain name of the client reporting data (tcp) and ssh (optional) in the `DNS` record of the corresponding domain, and turn on Orange Cloud to enable CDN.
+
+#### Visit Cloudflare website, add the domain name of the client reporting data (tcp) and ssh (optional) in the `DNS` record of the corresponding domain, and turn on Orange Cloud to enable CDN.
 -
-
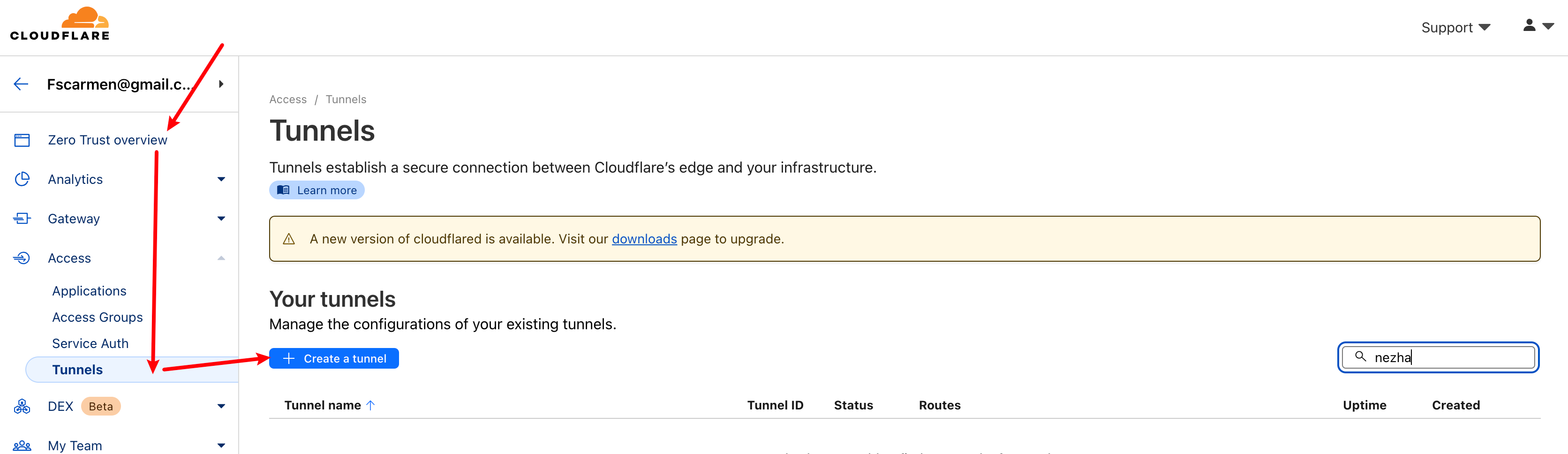
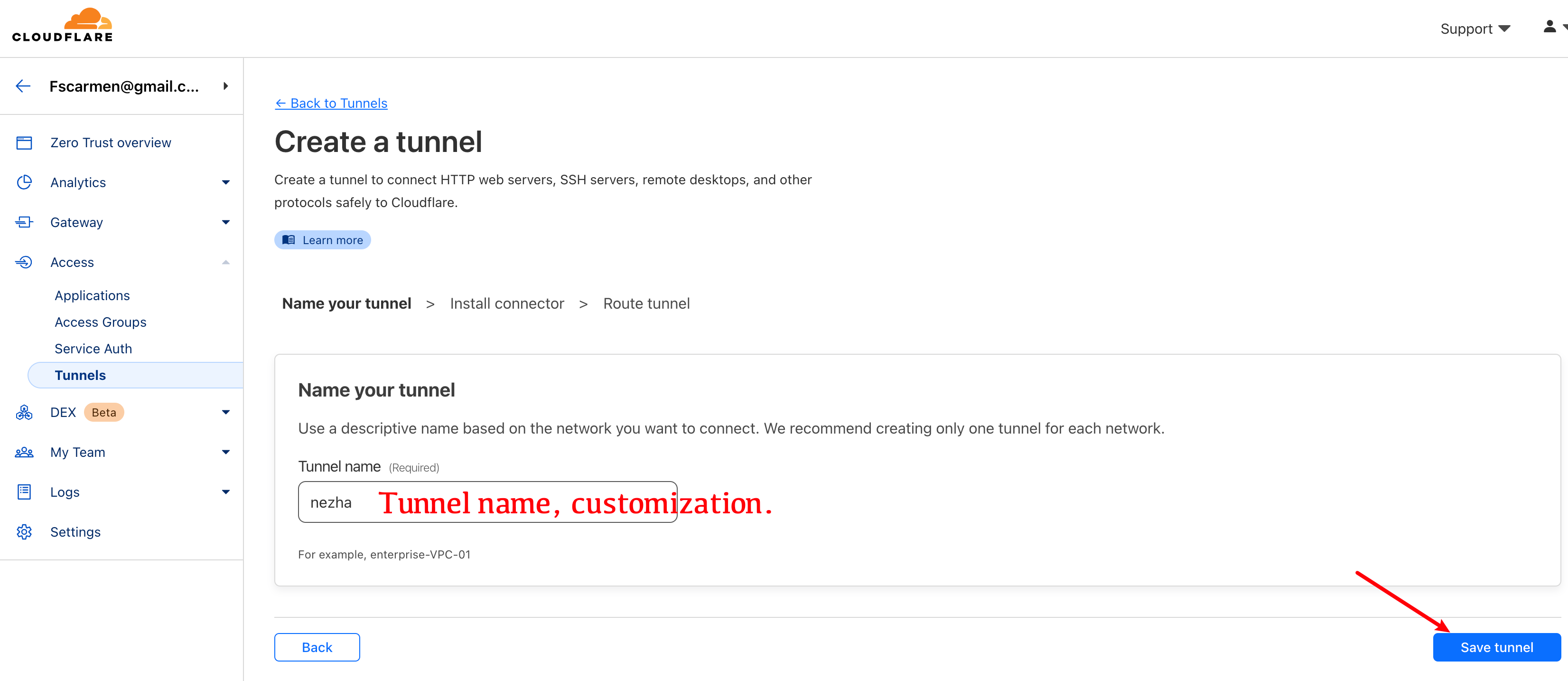
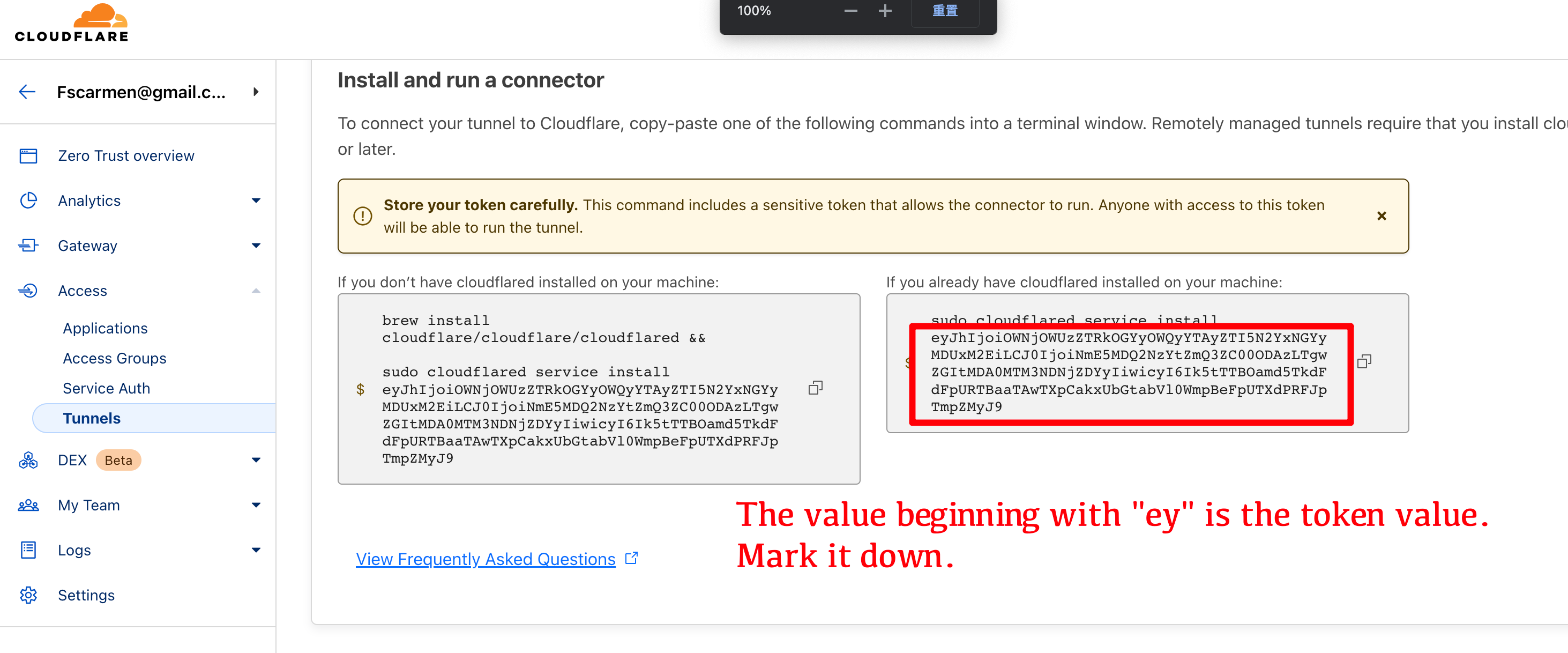
 +### (Methods 2 - Token): Manually generate Argo tunnel token information via Cloudflare website.
+#### Go to the cf website: https://dash.cloudflare.com/ and go to zero trust to generate token tunnels and messages.
+
+
+### (Methods 2 - Token): Manually generate Argo tunnel token information via Cloudflare website.
+#### Go to the cf website: https://dash.cloudflare.com/ and go to zero trust to generate token tunnels and messages.
+
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+## Prepare variables to be used
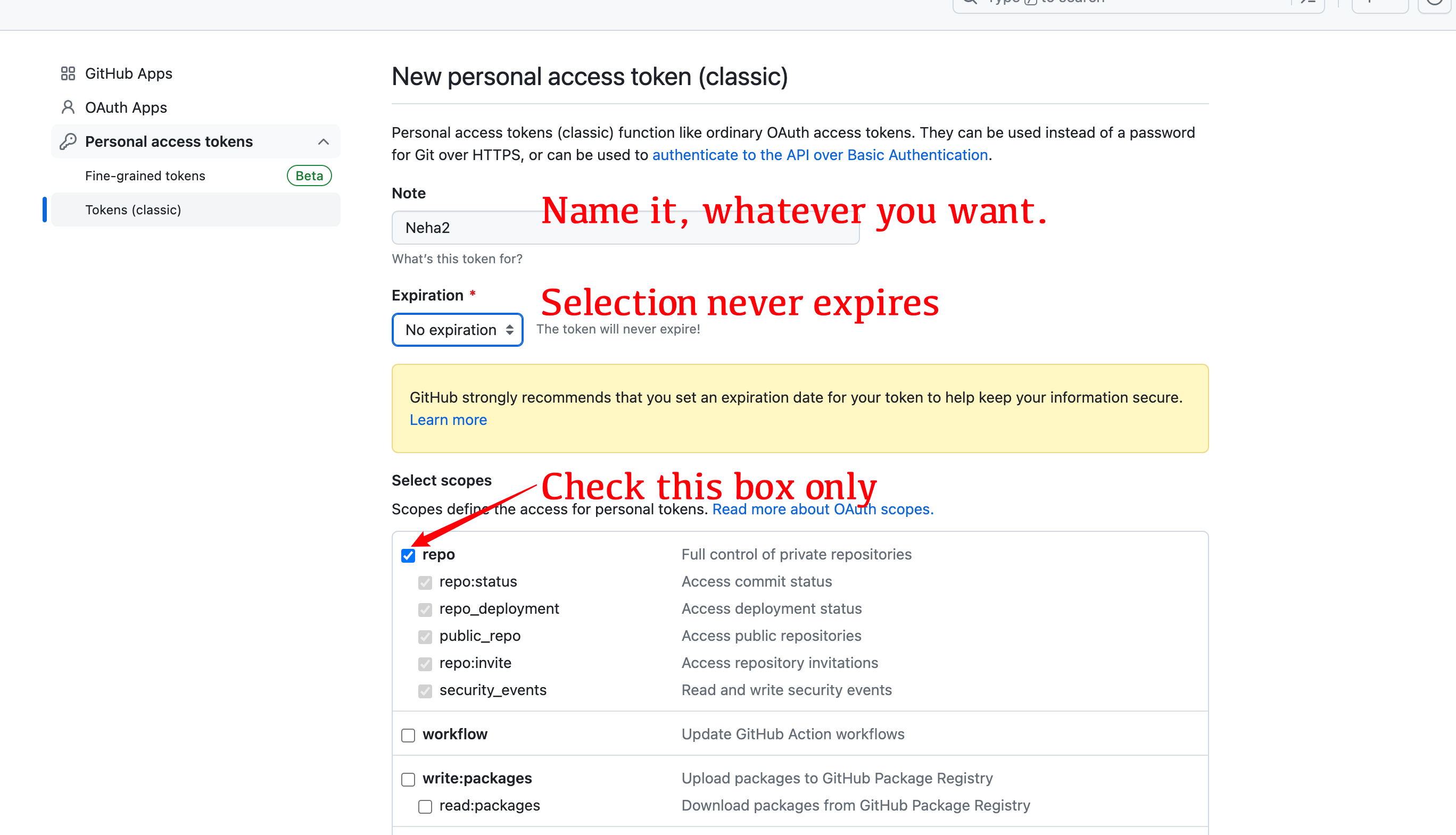
* Visit the Cloudflare website, select the domain name you want to use, and turn on the `network` option to turn the `gRPC` switch on.
+
+## Prepare variables to be used
* Visit the Cloudflare website, select the domain name you want to use, and turn on the `network` option to turn the `gRPC` switch on.
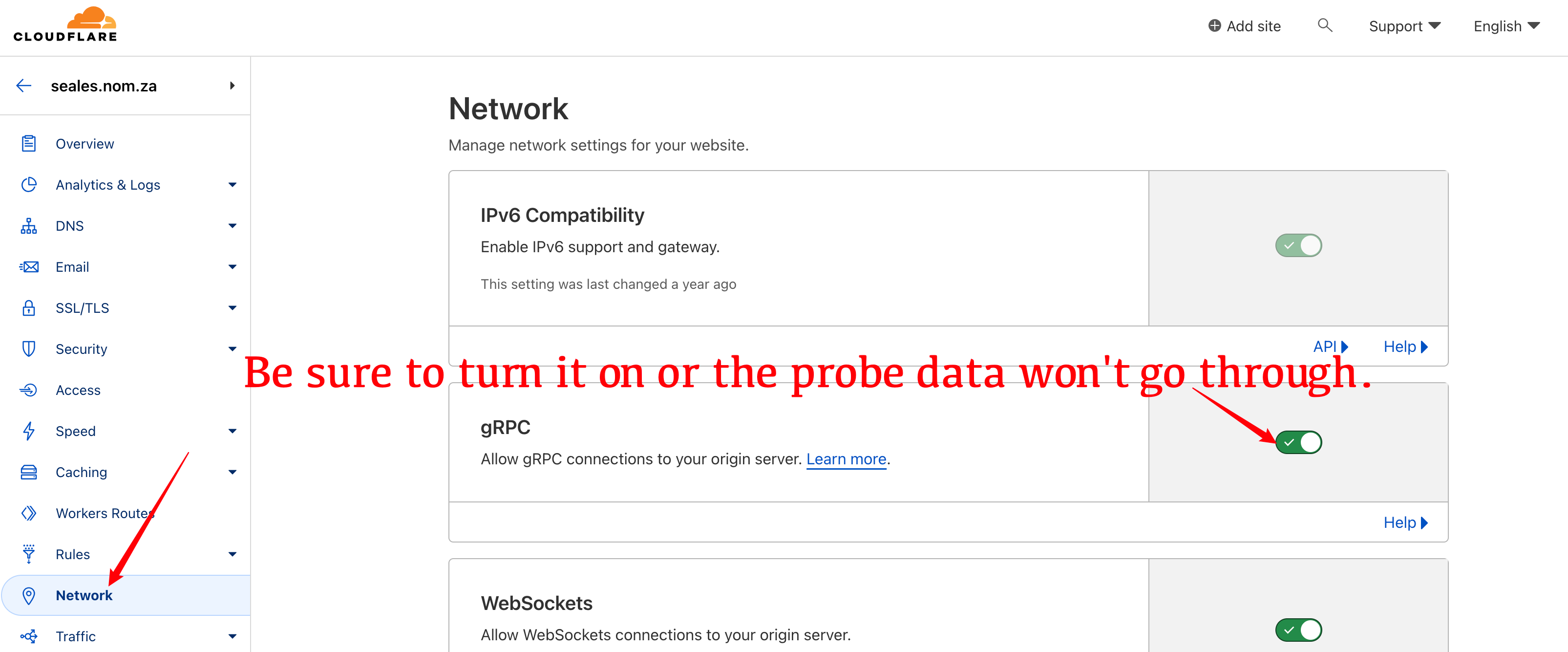 @@ -59,13 +75,11 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
Add `https://` to the beginning of the panel's domain name and `/oauth2/callback` to the end of the callback address.
@@ -59,13 +75,11 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
Add `https://` to the beginning of the panel's domain name and `/oauth2/callback` to the end of the callback address.
 -
-
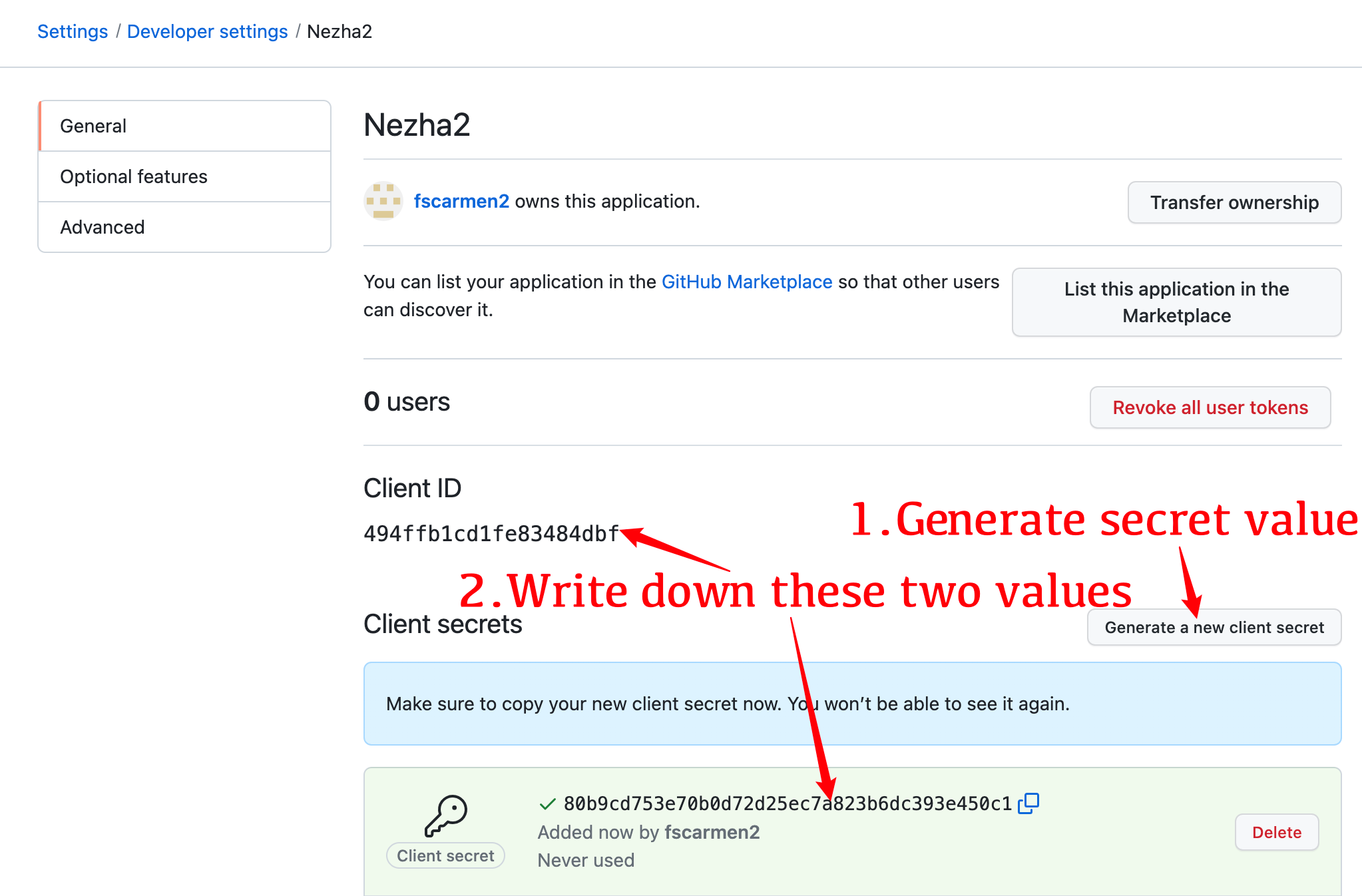 * Get a PAT (Personal Access Token) for github: https://github.com/settings/tokens/new
* Get a PAT (Personal Access Token) for github: https://github.com/settings/tokens/new
 -
-
 * Create a private github repository for backups: https://github.com/new
@@ -76,17 +90,17 @@ Add `https://` to the beginning of the panel's domain name and `/oauth2/callback
## PaaS Deployment Example
Image `fscarmen/argo-nezha:latest`, supports amd64 and arm64 architectures.
-Variables used
+Variables used
| Variable Name | Required | Remarks |
- | ------------ | ------ | ---- |
- | GH_USER | Yes | github username for panel admin authorization |
+ | ------------ | ------ | ---- |
+ | GH_USER | Yes | github username for panel admin authorization |
| GH_CLIENTID | yes | apply on github |
| GH_CLIENTSECRET | yes | apply on github |
| GH_BACKUP_USER | No | The github username for backing up Nezha's server-side database on github, if not filled in, it is the same as the account GH_USER for panel management authorization |
| GH_REPO | No | The github repository for backing up Nezha's server-side database files on github |
| GH_EMAIL | No | github's mailbox for git push backups to remote repositories |
| GH_PAT | No | github's PAT |
- | ARGO_JSON | Yes | Argo Json from https://fscarmen.cloudflare.now.cc |
+ | ARGO_AUTH | Yes | Argo Json from https://fscarmen.cloudflare.now.cc
* Create a private github repository for backups: https://github.com/new
@@ -76,17 +90,17 @@ Add `https://` to the beginning of the panel's domain name and `/oauth2/callback
## PaaS Deployment Example
Image `fscarmen/argo-nezha:latest`, supports amd64 and arm64 architectures.
-Variables used
+Variables used
| Variable Name | Required | Remarks |
- | ------------ | ------ | ---- |
- | GH_USER | Yes | github username for panel admin authorization |
+ | ------------ | ------ | ---- |
+ | GH_USER | Yes | github username for panel admin authorization |
| GH_CLIENTID | yes | apply on github |
| GH_CLIENTSECRET | yes | apply on github |
| GH_BACKUP_USER | No | The github username for backing up Nezha's server-side database on github, if not filled in, it is the same as the account GH_USER for panel management authorization |
| GH_REPO | No | The github repository for backing up Nezha's server-side database files on github |
| GH_EMAIL | No | github's mailbox for git push backups to remote repositories |
| GH_PAT | No | github's PAT |
- | ARGO_JSON | Yes | Argo Json from https://fscarmen.cloudflare.now.cc |
+ | ARGO_AUTH | Yes | Argo Json from https://fscarmen.cloudflare.now.cc
Argo token from Cloudflare official website |
| DATA_DOMAIN | Yes | Client-server communication argo domain name |
| WEB_DOMAIN | Yes | Panel argo domain |
| SSH_DOMAIN | No | ssh for argo domain |
@@ -94,11 +108,11 @@ Variables used
Koyeb
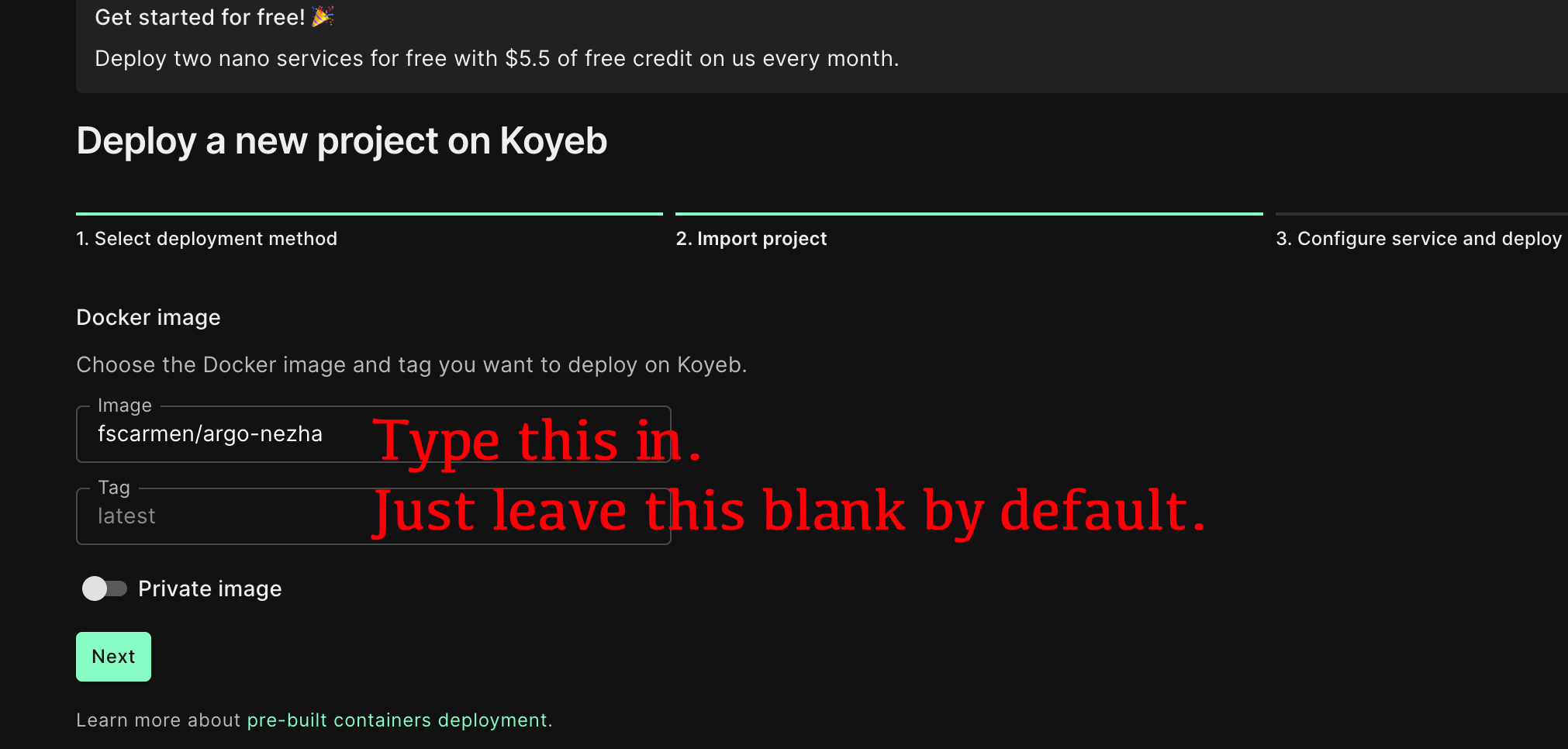
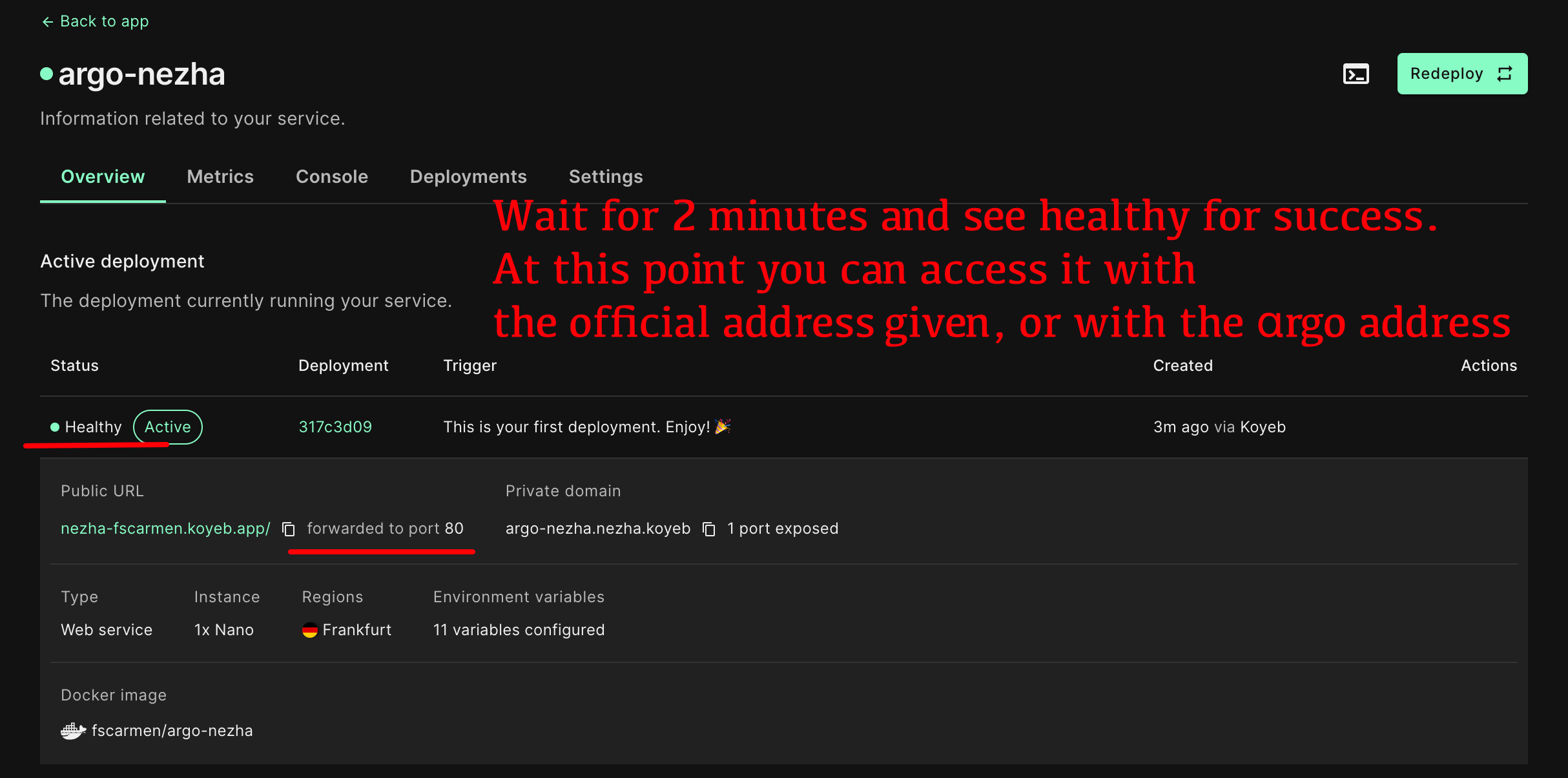
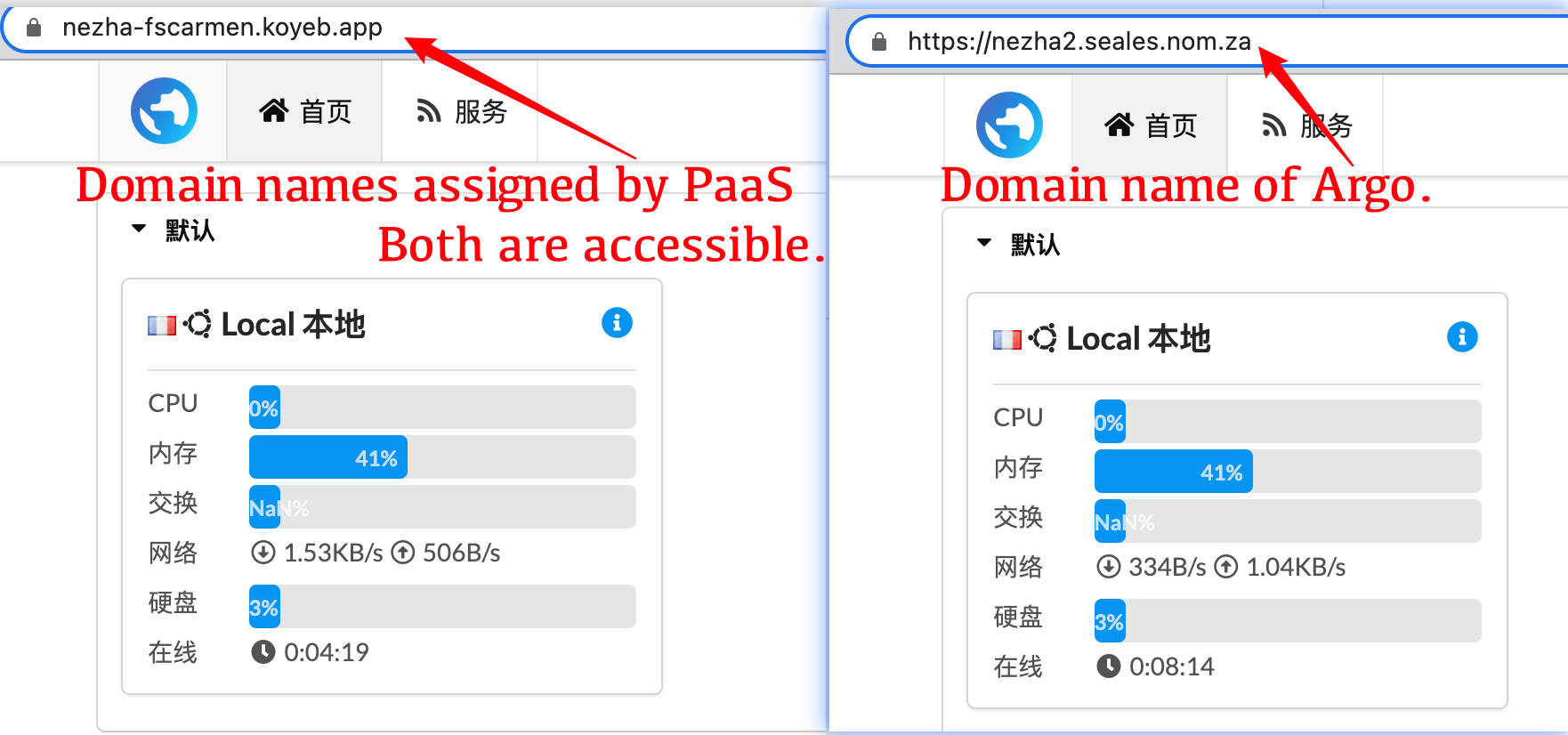
-[](https://app.koyeb.com/deploy?type=docker&name=nezha&ports=80;http;/&env[GH_USER]=&env[GH_CLIENTID]=&env[GH_CLIENTSECRET]=&env[GH_REPO]=&env[GH_EMAIL]=&env[GH_PAT]=&env[ARGO_JSON]=&env[DATA_DOMAIN]=&env[WEB_DOMAIN]=&env[SSH_DOMAIN]=&env[SSH_PASSWORD]=&image=docker.io/fscarmen/argo-nezha)
+[](https://app.koyeb.com/deploy?type=docker&name=nezha&ports=80;http;/&env[GH_USER]=&env[GH_CLIENTID]=&env[GH_CLIENTSECRET]=&env[GH_REPO]=&env[GH_EMAIL]=&env[GH_PAT]=&env[ARGO_AUTH]=&env[DATA_DOMAIN]=&env[WEB_DOMAIN]=&env[SSH_DOMAIN]=&env[SSH_PASSWORD]=&image=docker.io/fscarmen/argo-nezha)

 -
- +
+
 @@ -120,7 +134,7 @@ docker run -dit \
-e GH_REPO= \
-e GH_CLIENTID= \
-e GH_CLIENTSECRET= \
- -e ARGO_JSON='' \
+ -e ARGO_AUTH='' \
-e WEB_DOMAIN= \
-e DATA_DOMAIN= \
-e SSH_DOMAIN= \
@@ -143,7 +157,7 @@ services.
- GH_REPO=
- GH_CLIENTID=
- GH_CLIENTSECRET=
- - ARGO_JSON=''
+ - ARGO_AUTH=''
- WEB_DOMAIN=
- DATA_DOMAIN=
- SSH_DOMAIN=
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # Private key information for SSL/TLS certificate.
| |-- nezha.pem # SSL/TLS Privacy Enhancement Email
| `-- restore.sh # Restore backup scripts
-`-- dbfile # Record the name of the latest restore or backup file
+|-- dbfile # Record the name of the latest restore or backup file
+`-- version # Record the current panel app version
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* Intranet Penetration with Cloudflare Tunnel: https://blog.outv.im/2021/cloudflared-tunnel/
+* How to add your own Runner host to GitHub Actions: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner addition and startup: https://blog.csdn.net/sinat_32188225/article/details/125978331
## Disclaimer
@@ -120,7 +134,7 @@ docker run -dit \
-e GH_REPO= \
-e GH_CLIENTID= \
-e GH_CLIENTSECRET= \
- -e ARGO_JSON='' \
+ -e ARGO_AUTH='' \
-e WEB_DOMAIN= \
-e DATA_DOMAIN= \
-e SSH_DOMAIN= \
@@ -143,7 +157,7 @@ services.
- GH_REPO=
- GH_CLIENTID=
- GH_CLIENTSECRET=
- - ARGO_JSON=''
+ - ARGO_AUTH=''
- WEB_DOMAIN=
- DATA_DOMAIN=
- SSH_DOMAIN=
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # Private key information for SSL/TLS certificate.
| |-- nezha.pem # SSL/TLS Privacy Enhancement Email
| `-- restore.sh # Restore backup scripts
-`-- dbfile # Record the name of the latest restore or backup file
+|-- dbfile # Record the name of the latest restore or backup file
+`-- version # Record the current panel app version
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* Intranet Penetration with Cloudflare Tunnel: https://blog.outv.im/2021/cloudflared-tunnel/
+* How to add your own Runner host to GitHub Actions: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner addition and startup: https://blog.csdn.net/sinat_32188225/article/details/125978331
## Disclaimer
 +## Argo 认证的获取方式: json 或 token
+Argo 隧道认证方式有 json 和 token,使用两个方式其中之一
-## 准备需要用的变量
-* 通过 Cloudflare Json 生成网轻松获取 Argo 隧道信息: https://fscarmen.cloudflare.now.cc
+### (方式 1 - Josn):
+#### 通过 Cloudflare Json 生成网轻松获取 Argo 隧道 json 信息: https://fscarmen.cloudflare.now.cc
-
+## Argo 认证的获取方式: json 或 token
+Argo 隧道认证方式有 json 和 token,使用两个方式其中之一
-## 准备需要用的变量
-* 通过 Cloudflare Json 生成网轻松获取 Argo 隧道信息: https://fscarmen.cloudflare.now.cc
+### (方式 1 - Josn):
+#### 通过 Cloudflare Json 生成网轻松获取 Argo 隧道 json 信息: https://fscarmen.cloudflare.now.cc
- +
+ -
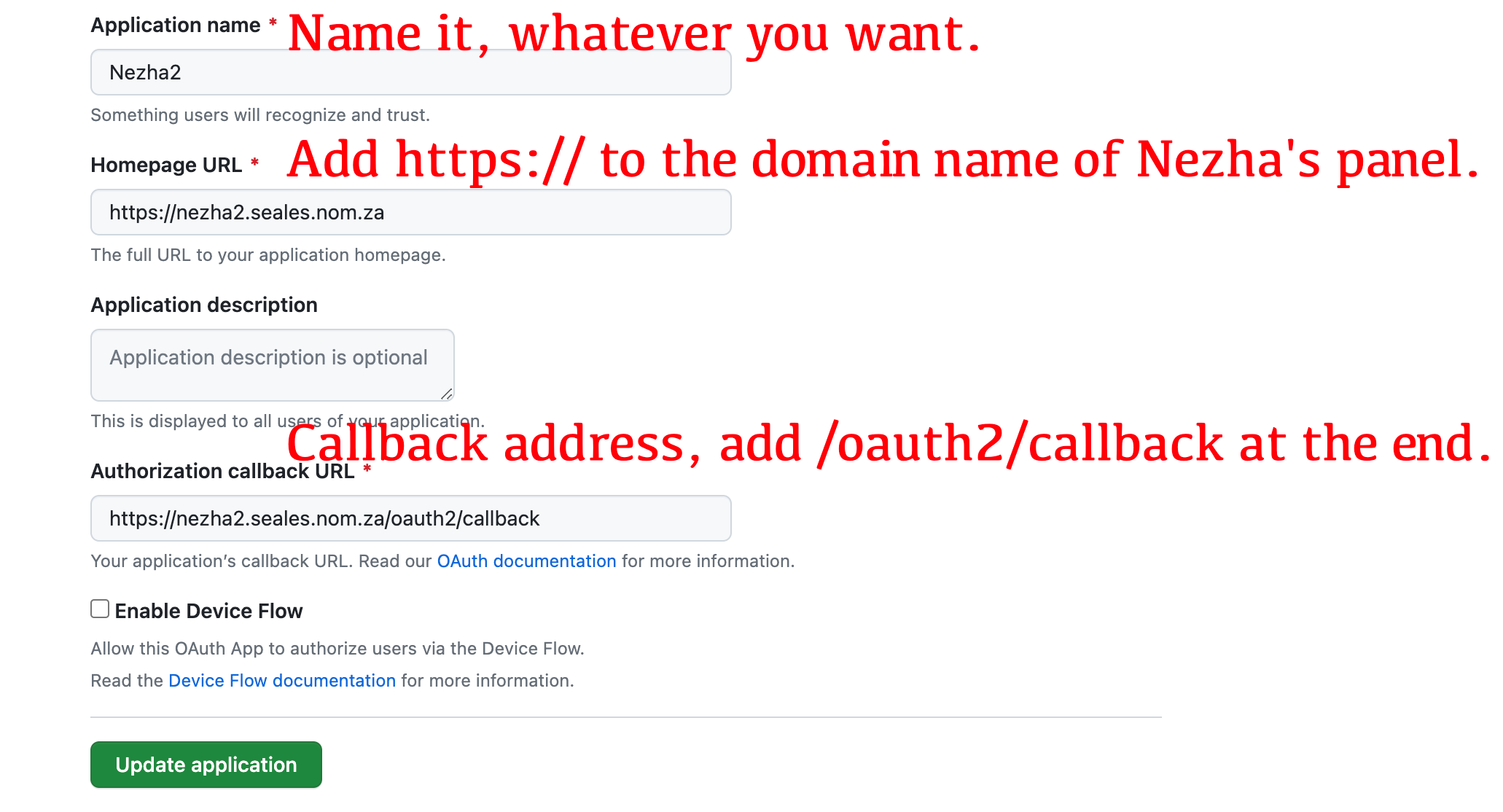
* 获取 github 认证授权: https://github.com/settings/applications/new
面板域名加上 `https://` 开头,回调地址再加上 `/oauth2/callback` 结尾
-
* 获取 github 认证授权: https://github.com/settings/applications/new
面板域名加上 `https://` 开头,回调地址再加上 `/oauth2/callback` 结尾
 -
-
 * 获取 github 的 PAT (Personal Access Token): https://github.com/settings/tokens/new
* 获取 github 的 PAT (Personal Access Token): https://github.com/settings/tokens/new
 -
-
 * 创建 github 用于备份的私库: https://github.com/new
@@ -77,7 +90,7 @@
## PaaS 部署实例
镜像 `fscarmen/argo-nezha:latest` , 支持 amd64 和 arm64 架构
-用到的变量
+用到的变量
| 变量名 | 是否必须 | 备注 |
| ------------ | ------ | ---- |
| GH_USER | 是 | github 的用户名,用于面板管理授权 |
@@ -87,7 +100,7 @@
| GH_REPO | 否 | 在 github 上备份哪吒服务端数据库文件的 github 库 |
| GH_EMAIL | 否 | github 的邮箱,用于备份的 git 推送到远程库 |
| GH_PAT | 否 | github 的 PAT |
- | ARGO_JSON | 是 | 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json |
+ | ARGO_AUTH | 是 | Json: 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json
* 创建 github 用于备份的私库: https://github.com/new
@@ -77,7 +90,7 @@
## PaaS 部署实例
镜像 `fscarmen/argo-nezha:latest` , 支持 amd64 和 arm64 架构
-用到的变量
+用到的变量
| 变量名 | 是否必须 | 备注 |
| ------------ | ------ | ---- |
| GH_USER | 是 | github 的用户名,用于面板管理授权 |
@@ -87,7 +100,7 @@
| GH_REPO | 否 | 在 github 上备份哪吒服务端数据库文件的 github 库 |
| GH_EMAIL | 否 | github 的邮箱,用于备份的 git 推送到远程库 |
| GH_PAT | 否 | github 的 PAT |
- | ARGO_JSON | 是 | 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json |
+ | ARGO_AUTH | 是 | Json: 从 https://fscarmen.cloudflare.now.cc 获取的 Argo Json
 +
+

 @@ -121,7 +135,7 @@ docker run -dit \
-e GH_REPO=<填自定义的> \
-e GH_CLIENTID=<填获取的> \
-e GH_CLIENTSECRET=<填获取的> \
- -e ARGO_JSON='<填获取的>' \
+ -e ARGO_AUTH='<填获取的 Argo json 或者 token>' \
-e WEB_DOMAIN=<填自定义的> \
-e DATA_DOMAIN=<填自定义的> \
-e SSH_DOMAIN=<填自定义的> \
@@ -144,7 +158,7 @@ services:
- GH_REPO=<填自定义的>
- GH_CLIENTID=<填获取的>
- GH_CLIENTSECRET=<填获取的>
- - ARGO_JSON='<填获取的>'
+ - ARGO_AUTH='<填获取的 Argo json 或者 token>'
- WEB_DOMAIN=<填自定义的>
- DATA_DOMAIN=<填自定义的>
- SSH_DOMAIN=<填自定义的>
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # SSL/TLS 证书的私钥信息
| |-- nezha.pem # SSL/TLS 隐私增强邮件
| `-- restore.sh # 还原备份脚本
-`-- dbfile # 记录最新的还原或备份文件名
+|-- dbfile # 记录最新的还原或备份文件名
+`-- version # 记录当前的面板 app 版本
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* 用 Cloudflare Tunnel 进行内网穿透: https://blog.outv.im/2021/cloudflared-tunnel/
+* 如何给 GitHub Actions 添加自己的 Runner 主机: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner 添加与启动: https://blog.csdn.net/sinat_32188225/article/details/125978331
## 免责声明:
diff --git a/docs/en_US/case/case5.md b/docs/en_US/case/case5.md
index 4ef74355..729b4f04 100644
--- a/docs/en_US/case/case5.md
+++ b/docs/en_US/case/case5.md
@@ -11,6 +11,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
# Catalog
- [Project Features](case5.md#project-features)
+- [How to get Argo authentication: json or token](case5.md#How-to-get-Argo-authentication-json-or-token)
- [Variables to be used](case5.md#prepare-variables-to-be-used)
- [PaaS Deployment Example](case5.md#paas-deployment-example)
- [VPS Deployment Example](case5.md#vps-deployment-example)
@@ -32,6 +33,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
* One Argo tunnel for multiple domains and protocols --- Create an intranet-penetrating Argo tunnel for three domains (hostname) and protocols, which can be used for panel access (http), client reporting (tcp) and ssh (optional).
* Nginx reverse proxy gRPC data port --- with a certificate for tls termination, then Argo's tunnel configuration with https service pointing to this reverse proxy, enable http2 back to the source, grpc(nezha)->h2(nginx)->argo->cf cdn edge->agent
* Daily automatic backup --- every day at 04:00 BST, the entire Nezha panel folder is automatically backed up to a designated private github repository, including panel themes, panel settings, probe data and tunnel information, the backup retains nearly 5 days of data; the content is so important that it must be placed in the private repository.
+* Automatic daily panel update -- the latest official panel version is automatically detected every day at 4:00 BST, and updated when there is an upgrade.
* Manual/automatic restore backup --- check the content of online restore file once a minute, and restore immediately when there is any update.
* Default built-in local probes --- can easily monitor their own server information
* More secure data --- Argo Tunnel uses TLS encrypted communication to securely transmit application traffic to the Cloudflare network, improving application security and reliability. In addition, Argo Tunnel protects against network threats such as IP leaks and DDoS attacks.
@@ -39,17 +41,31 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
@@ -121,7 +135,7 @@ docker run -dit \
-e GH_REPO=<填自定义的> \
-e GH_CLIENTID=<填获取的> \
-e GH_CLIENTSECRET=<填获取的> \
- -e ARGO_JSON='<填获取的>' \
+ -e ARGO_AUTH='<填获取的 Argo json 或者 token>' \
-e WEB_DOMAIN=<填自定义的> \
-e DATA_DOMAIN=<填自定义的> \
-e SSH_DOMAIN=<填自定义的> \
@@ -144,7 +158,7 @@ services:
- GH_REPO=<填自定义的>
- GH_CLIENTID=<填获取的>
- GH_CLIENTSECRET=<填获取的>
- - ARGO_JSON='<填获取的>'
+ - ARGO_AUTH='<填获取的 Argo json 或者 token>'
- WEB_DOMAIN=<填自定义的>
- DATA_DOMAIN=<填自定义的>
- SSH_DOMAIN=<填自定义的>
@@ -213,7 +227,8 @@ tar czvf dashboard.tar.gz /dashboard
| |-- nezha.key # SSL/TLS 证书的私钥信息
| |-- nezha.pem # SSL/TLS 隐私增强邮件
| `-- restore.sh # 还原备份脚本
-`-- dbfile # 记录最新的还原或备份文件名
+|-- dbfile # 记录最新的还原或备份文件名
+`-- version # 记录当前的面板 app 版本
```
@@ -224,6 +239,8 @@ tar czvf dashboard.tar.gz /dashboard
* Akkia's Blog: https://blog.akkia.moe/
* HiFeng's Blog: https://www.hicairo.com/
* 用 Cloudflare Tunnel 进行内网穿透: https://blog.outv.im/2021/cloudflared-tunnel/
+* 如何给 GitHub Actions 添加自己的 Runner 主机: https://cloud.tencent.com/developer/article/1756690
+* github self-hosted runner 添加与启动: https://blog.csdn.net/sinat_32188225/article/details/125978331
## 免责声明:
diff --git a/docs/en_US/case/case5.md b/docs/en_US/case/case5.md
index 4ef74355..729b4f04 100644
--- a/docs/en_US/case/case5.md
+++ b/docs/en_US/case/case5.md
@@ -11,6 +11,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
# Catalog
- [Project Features](case5.md#project-features)
+- [How to get Argo authentication: json or token](case5.md#How-to-get-Argo-authentication-json-or-token)
- [Variables to be used](case5.md#prepare-variables-to-be-used)
- [PaaS Deployment Example](case5.md#paas-deployment-example)
- [VPS Deployment Example](case5.md#vps-deployment-example)
@@ -32,6 +33,7 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
* One Argo tunnel for multiple domains and protocols --- Create an intranet-penetrating Argo tunnel for three domains (hostname) and protocols, which can be used for panel access (http), client reporting (tcp) and ssh (optional).
* Nginx reverse proxy gRPC data port --- with a certificate for tls termination, then Argo's tunnel configuration with https service pointing to this reverse proxy, enable http2 back to the source, grpc(nezha)->h2(nginx)->argo->cf cdn edge->agent
* Daily automatic backup --- every day at 04:00 BST, the entire Nezha panel folder is automatically backed up to a designated private github repository, including panel themes, panel settings, probe data and tunnel information, the backup retains nearly 5 days of data; the content is so important that it must be placed in the private repository.
+* Automatic daily panel update -- the latest official panel version is automatically detected every day at 4:00 BST, and updated when there is an upgrade.
* Manual/automatic restore backup --- check the content of online restore file once a minute, and restore immediately when there is any update.
* Default built-in local probes --- can easily monitor their own server information
* More secure data --- Argo Tunnel uses TLS encrypted communication to securely transmit application traffic to the Cloudflare network, improving application security and reliability. In addition, Argo Tunnel protects against network threats such as IP leaks and DDoS attacks.
@@ -39,17 +41,31 @@ Mirror backup (not live update): [Argo-Nezha-Service-Container](https://github.c
 -## Prepare variables to be used
-* Easily get Argo tunnel information through Cloudflare Json generation network: https://fscarmen.cloudflare.now.cc
+## How to get Argo authentication: json or token
+The Argo Tunnel authentication methods are json and token, use one of the two methods.
-
-## Prepare variables to be used
-* Easily get Argo tunnel information through Cloudflare Json generation network: https://fscarmen.cloudflare.now.cc
+## How to get Argo authentication: json or token
+The Argo Tunnel authentication methods are json and token, use one of the two methods.
-